Track
Imagine a customer calling, confused because their money was deducted but never credited to the recipient, or an order went through without updating the inventory. These problems happen when data integrity isn’t enforced. That’s where ACID principles come in.
ACID principles are enforced to ensure every transaction is processed reliably, keeping data safe and systems running smoothly. Understanding these principles is key to building reliable and fault-tolerant systems.
In this guide, you'll learn:
- Why ACID transactions matter.
- How they ensure the smooth functioning of database systems.
- Real-world examples of their use.
- Best practices for working with them.
Let’s get into it!
What are ACID Transactions?
ACID transactions refer to four properties that ensure the reliable processing of database transactions. The four principles are:
- Atomicity
- Consistency
- Isolation
- Durability
These principles guarantee that transactions are executed fully, without partial updates or data corruption, even in the case of system failures. ACID transactions are critical in scenarios where data integrity is paramount.
In banking transactions, ACID guarantees that money is either fully transferred or not at all, preventing issues like partial transfers or double deductions. In e-commerce, ACID principles ensure customer orders are processed correctly, payments are completed, and inventory updates reflect real-time stock levels. Similarly, in inventory management systems, ACID maintains consistency by preventing stock discrepancies due to concurrent transactions.
Breaking Down the ACID Properties
Each of the four properties that comprise the ACID principles addresses a specific transaction management aspect.
Let's explore these properties to understand how they contribute to robust database systems.
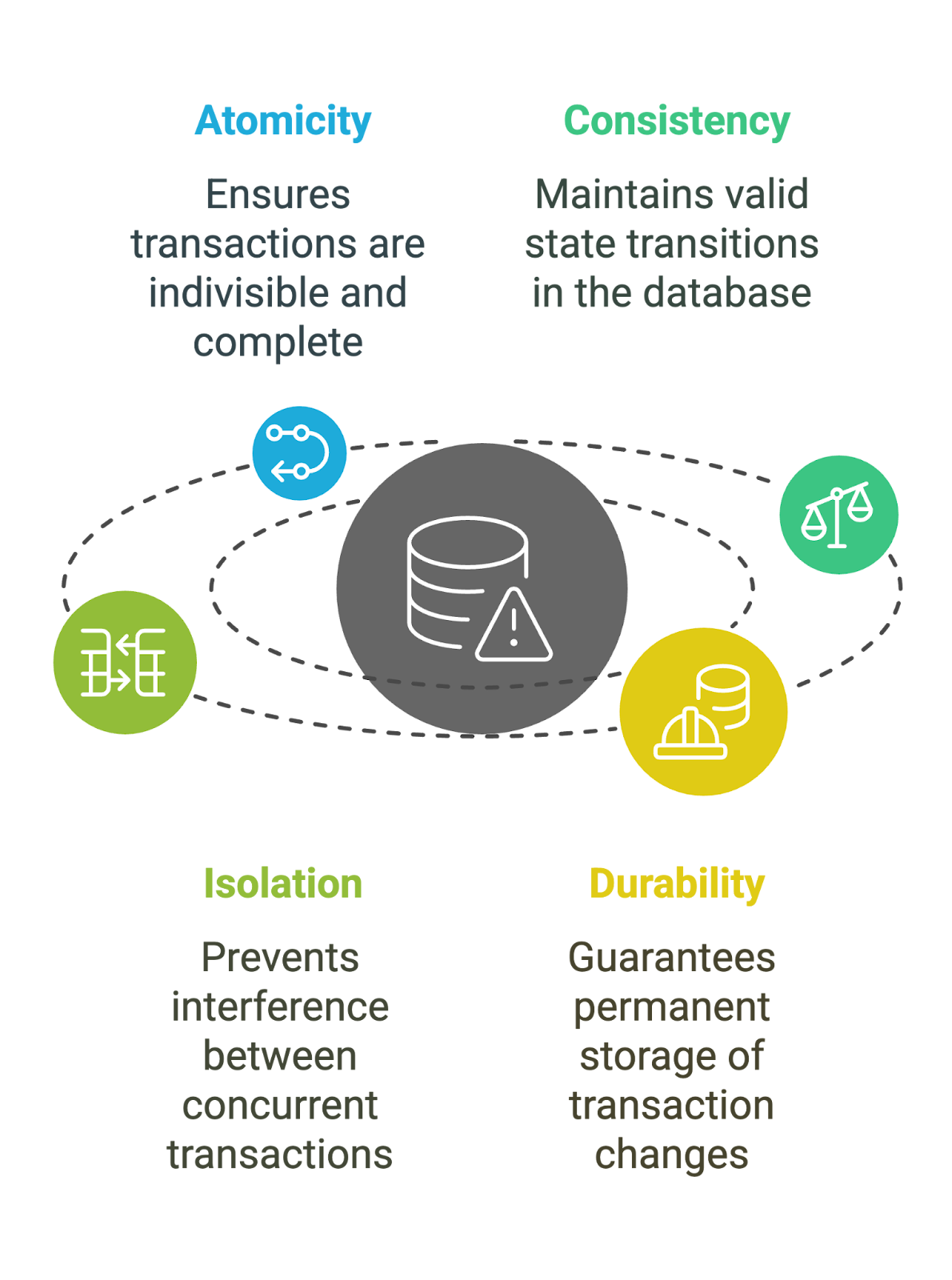
Atomicity
Atomicity guarantees that a transaction is treated as a single, indivisible unit. This means that all operations within a transaction must either be completed fully or not at all. If any part of the transaction fails, the system rolls back the entire transaction, ensuring no partial updates occur.
Example: In a banking transaction, atomicity ensures that both operations are completed successfully when money is debited from one account and credited to another. If either the debit or credit fails, the transaction is entirely reversed.
Consistency
Consistency ensures that a transaction brings the database from one valid state to another while adhering to predefined rules or constraints. After completing a transaction, the data must meet all the database's integrity rules.
Example: In banking, consistency ensures that the total balance across all accounts remains unchanged after a transfer. For example, if $100 is transferred between accounts, the sum of both account balances remains the same to preserve the accounting rules.
Isolation
Isolation prevents transactions from interfering with each other. When multiple transactions are executed simultaneously, isolation ensures they don't affect each other’s outcomes. Each transaction must be isolated to avoid conflicts – especially in high-concurrency environments.
Example: If two customers attempt to purchase the last item in stock at the same time, isolation ensures that only one transaction will succeed, and the inventory is updated correctly to reflect the change.
Durability
Durability guarantees that once a transaction is completed, its changes are permanently stored in the database (even if the system crashes immediately afterward). This ensures that the data remains intact and accessible after failures.
Example: In an e-commerce system, durability ensures that the order data is saved to the database after a customer completes a purchase. Even if the server crashes moments later, the purchase record remains intact and can be retrieved when the system is restored.
ACID properties. Image by Author
ACID Transactions in Relational Databases
Most relational databases are built with ACID principles at their core. This means they are designed to maintain data accuracy and reliability.
In this section, let’s explore how databases implement ACID properties.
For those new to relational databases, this Introduction to Relational Databases in SQL course is perfect for building a strong foundation.
How ACID is implemented in SQL databases
Traditional SQL databases enforce ACID properties through transaction control mechanisms such as SQL commands like BEGIN, COMMIT, and ROLLBACK. These commands manage transactions, while transaction logs and locks ensure data integrity.
For example:
- Atomicity is managed using
ROLLBACKin case of errors, preventing partial updates. - Consistency is enforced via constraints (e.g., foreign keys, unique keys) to maintain data integrity.
- Isolation is implemented through locks to avoid conflicts between concurrent transactions.
- Durability is achieved by persisting transactions, ensuring that they are not lost once committed, even in the event of a failure.
ACID compliance in different database systems
Most SQL databases come with built-in ACID compliance to maintain transactional integrity. Systems like MySQL, PostgreSQL, Oracle, and Microsoft SQL Server use transaction logs (e.g., Write-Ahead Logging in PostgreSQL) and locking protocols (e.g., two-phase locking) to enforce ACID properties. These mechanisms help preserve data integrity for each transaction.
More specifically:
- MySQL: Uses the InnoDB storage engine, which supports ACID-compliant transactions. It manages atomicity and durability via a redo log that can roll back failed transactions and recover committed ones.
- PostgreSQL: Leverages Write-Ahead Logging (WAL) to ensure durability and consistency by recording changes to a log before applying them to the database.
- Oracle: Employs rollback segments and undo logs to ensure atomicity and durability, providing robust transaction control.
Working with SQL Server? This course on Transactions and Error Handling in SQL Server is a great way to master transaction control and ensure data integrity.
Example SQL transaction with ACID compliance
Here’s a simple SQL example of a transaction in PostgreSQL that adheres to ACID principles.
This example demonstrates transferring money between two accounts to ensure that the transaction either fully completes or fully rolls back in case of failure:
BEGIN;
-- Step 1: Debit $500 from Account A
UPDATE accounts
SET balance = balance - 500
WHERE account_id = 'A';
-- Step 2: Credit $500 to Account B
UPDATE accounts
SET balance = balance + 500
WHERE account_id = 'B';
-- Commit the transaction if both steps succeed
COMMIT;
-- Rollback the transaction if an error occurs
ROLLBACK;In this transaction:
- If either update fails, the transaction will be rolled back.
- The database remains valid, as the total balance across both accounts is unchanged.
- If another transaction attempts to modify these accounts concurrently, locking guarantees that one completes before the other.
- Once the transaction is committed, the changes are saved permanently, even if the system crashes afterward.
If you're just getting started with SQL, this Introduction to SQL course will help you grasp the fundamentals and start writing queries with confidence.
Associate Data Engineer in SQL
ACID vs. BASE Transactions in NoSQL Databases
While ACID transactions have long been the gold standard for ensuring data integrity in relational databases, NoSQL databases often prioritize flexibility and scalability over strict transactional consistency. This shift has led to adopting BASE as an alternative to ACID in certain use cases.
Let’s explore BASE, its differences with ACID, and when each approach is preferred.
What is BASE?
BASE is an acronym for Basically Available, Soft state, Eventual consistency. It defines a set of properties designed for NoSQL databases, focusing on availability and flexibility over strict consistency.
Let’s define the principles:
- Basically available: The system guarantees availability, meaning it will respond to requests even if some parts of the system are down or unreachable.
- Soft state: Due to asynchronous updates, the system's state may change over time, even without input.
- Eventual consistency: Data will eventually become consistent, but there may be periods when it is temporarily inconsistent.
Differences between ACID and BASE
The primary differences between ACID and BASE revolve around the trade-offs made in terms of consistency, availability, and performance:
Consistency
ACID ensures that the database is always consistent after a transaction, with strict rules for maintaining data integrity. On the other hand, BASE sacrifices strict consistency in favor of availability and performance. This enables temporary inconsistencies until the system eventually reaches a consistent state.
Availability
ACID systems prioritize consistency and durability over availability, so they may become unavailable during certain failures. BASE systems are designed for high availability. This ensures that the system remains responsive even during network partitions or failures.
Scalability
ACID systems may face challenges when scaling horizontally across distributed systems, as maintaining strict consistency can be resource-intensive. BASE systems are more scalable and are often built for horizontal scaling to handle large volumes of data and traffic with less emphasis on immediate consistency.
Use cases for ACID and BASE
ACID transactions are ideal when data consistency is critical, for example:
- Financial transactions: Accuracy and consistency are crucial when transferring money or processing payments.
- Inventory systems: Ensuring stock levels are updated accurately is vital to avoid overselling or discrepancies.
- Order processing: To satisfy customers in e-commerce, orders need to be processed correctly and consistently.
BASE transactions are preferred when scalability, high availability, and performance outweigh the need for strict consistency, for example:
- Social media feeds: Data consistency is less critical, and temporary inconsistencies in posts or likes are acceptable as long as the system remains responsive.
- Content delivery networks: Serving content to users with minimal latency is prioritized over consistency.
ACID vs BASE: A comparison table
|
Feature |
ACID |
BASE |
|
Full Form |
Atomicity, Consistency, Isolation, Durability |
Basically Available, Soft state, Eventually consistent |
|
Core principle |
Ensures reliable, consistent transactions |
Prioritizes availability and performance over strict consistency |
|
Consistency model |
Strict consistency |
Eventual consistency |
|
Data integrity |
High – Guarantees data integrity at all times |
Lower – Allows temporary inconsistencies |
|
Transaction handling |
Transactions must complete fully or not at all |
Best-effort transactions – may be incomplete or inconsistent temporarily |
|
Scalability |
Limited – Works best with monolithic or traditional relational databases |
High – Designed for distributed, scalable systems |
|
Latency |
Higher – Due to strict consistency requirements |
Lower – Allows for faster response times |
|
Use cases |
Financial transactions, inventory management, order processing |
Social media platforms, real-time analytics, content delivery networks |
If you're curious about how BASE principles apply in NoSQL databases, check out this NoSQL Concepts course—it’s a great starting point for understanding the trade-offs.
Common Challenges with ACID Transactions
Implementing ACID transactions doesn’t come without challenges. These challenges are particularly evident in high-transaction environments, distributed systems, and when managing concurrent transactions.
In this section, we will dive into the key issues faced when working with ACID transactions.
Performance costs of ACID transactions
One of the primary trade-offs when using ACID transactions is performance. Ensuring atomicity, consistency, and durability comes at a cost — particularly when the database handles high transaction volumes.
The requirements for maintaining these properties can slow down operations in the following ways:
- Atomicity requires that all steps within a transaction be executed as a single unit, which means the system must ensure that if one part of the transaction fails, the entire transaction is rolled back. This rollback process can be resource-intensive.
- Consistency demands that transactions always bring the database to a valid state, often involving checking constraints, triggers, and business rules. These additional checks can increase the processing time of each transaction.
- Durability ensures that the changes are permanently saved once a transaction is committed, often requiring writes to multiple locations, including transaction logs and disk storage. This persistent storage process can slow down the system's overall throughput.
As the transaction volume increases, these processes can lead to bottlenecks that limit the system's scalability and responsiveness.
Difficulty in scaling ACID-compliant databases across distributed systems
ACID principles are traditionally designed for single-node or centralized systems, where data integrity and transactional consistency are easier to manage. However, as databases grow in scale—especially across geographically distributed clusters—maintaining ACID properties becomes more complex.
- Distributed transactions: In a distributed environment, transactions may span multiple nodes or locations. Ensuring that all participating nodes agree on the outcome of a transaction can be difficult, especially when latency or network partitions occur. Techniques like the two-phase commit protocol are often used but can add overhead and complexity.
- Data replication: ACID-compliant databases often replicate data across multiple servers to ensure durability. However, synchronizing this data and ensuring all replicas are consistent can be slow and resource-intensive. Network delays and server failures can further complicate the consistency of the replicated data.
Scaling ACID-compliant databases requires careful management of consistency and durability across all nodes, which is problematic (particularly for highly dynamic or globally distributed systems).
Managing concurrent transactions while preserving isolation
Concurrent transactions pose another challenge for ACID-compliant databases in multi-user environments. Isolation ensures that concurrent transactions do not interfere with one another, but achieving this requires mechanisms to manage and control access to data.
The most common method of managing concurrency is through locking mechanisms, but these come with their own set of challenges:
- Locking: Databases employ locks (e.g., row-level and table-level locks) to prevent conflicting transactions from accessing the same data simultaneously. Locking ensures isolation but can lead to deadlocks, where two or more transactions are waiting for each other to release locks.
- Lock contention: High levels of concurrency can lead to lock contention, where transactions frequently block one another, slowing down the overall system. As the number of transactions increases, managing locks becomes more complex and can negatively impact performance.
- Transaction rollback: If a deadlock occurs or a conflict is detected, one of the transactions may need to be rolled back, which leads to wasted resources and reduced throughput.
Best Practices for Working with ACID Transactions
Applying best practices can significantly benefit your system's longevity in high-volume systems or complex environments.
Here are some key practices for working with ACID transactions effectively.
Implement proper transaction management
One of the most important best practices is implementing transactions only when necessary. Yes, ACID properties are essential for operations that require data integrity, but using transactions for every database operation can introduce unnecessary overhead and performance bottlenecks.
- Minimize transaction scope: Restrict the scope of each transaction to the critical operations that absolutely require atomicity and consistency. Avoid wrapping unnecessary read-only operations in.
- Use smaller transactions: Break larger, complex operations into smaller transactions if possible. This can reduce the amount of work done per transaction.
- Commit or roll back quickly: Always ensure that transactions are committed or rolled back as soon as possible to free up resources and avoid long-running locks.
Essentially, the key is to focus only on critical operations. This will secure the integrity of your database without incurring excessive overhead.
Optimize for concurrency
Optimizing database configurations and applying concurrency controls are essential for maintaining performance while ensuring that multiple transactions can run simultaneously without compromising the isolation property.
- Transaction isolation levels: Choose the appropriate isolation level based on your application's needs. For example,
READ COMMITTEDis suitable for many applications, butSERIALIZABLEmay be needed for scenarios where strict isolation is necessary. Be aware that higher isolation levels can increase contention and reduce throughput. - Locking mechanisms: Properly configure locking mechanisms to ensure data integrity while allowing high levels of concurrency. For example, row-level locking (instead of table-level locking) can help prevent bottlenecks when multiple transactions attempt to access the same data.
- Optimistic concurrency control: In some cases, you may implement optimistic concurrency control to avoid locking entirely. This approach assumes that conflicts will be rare and only validates data at commit time, which can be more efficient than locking records during the transaction.
Optimizing concurrency safeguards your system and keeps it responsive (even when handling simultaneous transactions).
Monitor and log transactions
Monitoring and logging must be done to keep you informed of the health and efficiency of your database system.
- Monitor transaction performance: Use tools to track transaction performance in real time. Look for slow queries, excessive locks, or frequent rollbacks, which could indicate transaction management or database configuration issues.
- Log errors and exceptions: Ensure that all transaction failures, rollbacks, and conflicts are logged for further analysis. This helps identify recurring problems, troubleshoot issues, and make improvements.
- Analyze transaction throughput: Track the number of transactions being processed and assess whether the system handles the load effectively. If the number of transactions exceeds what the system can handle, you may need to optimize your configuration or distribute the load more evenly.
Effective monitoring and logging allow you to manage your database proactively. The more you know about your database system, the more you can update it to ensure it continues to meet your application's demands.
Conclusion
In this article, we explored the critical principles of ACID transactions. We discussed the importance of these properties in scenarios like financial transactions, e-commerce orders, and inventory systems and highlighted how they are implemented in popular SQL databases.
Additionally, we examined the differences between ACID and BASE transactions, the challenges of scaling ACID-compliant systems, and best practices for managing transactions efficiently.
If you want to dive deeper into how ACID transactions work in PostgreSQL, I highly recommend this course on Transactions and Error Handling in PostgreSQL.
Become a Data Engineer
FAQs
How do ACID transactions work in distributed databases?
In distributed databases, achieving strict ACID compliance can be challenging due to network delays and partitioning issues. Technologies like Two-Phase Commit (2PC) and Three-Phase Commit (3PC) help coordinate transactions across multiple nodes, ensuring consistency. However, they introduce latency and potential bottlenecks, which is why some distributed databases prefer BASE over ACID. Newer approaches, like Google's Spanner and CockroachDB, use distributed consensus protocols like Paxos or Raft to maintain strong consistency while scaling globally.
Can ACID transactions be optimized for performance?
Yes, performance optimizations for ACID transactions include:
- Batching operations: Grouping multiple writes into a single transaction reduces overhead.
- Using indexes efficiently: Optimizing queries with proper indexing minimizes transaction duration.
- Optimistic concurrency control: Reduces lock contention by assuming transactions won’t conflict and validating at commit time.
- Tuning isolation levels: Lower isolation levels (e.g., Read Committed instead of Serializable) can improve performance while balancing consistency needs.
What is the difference between ACID transactions and idempotent operations?
ACID transactions ensure that each transaction is executed exactly once and fully completed (or fully rolled back). In contrast, idempotent operations guarantee that repeated executions yield the same result without unintended side effects. For example, updating a record (UPDATE users SET balance = 100 WHERE id = 1) is idempotent, but incrementing a balance (UPDATE users SET balance = balance + 100 WHERE id = 1) is not idempotent unless wrapped in an ACID transaction to prevent race conditions.
How do modern databases balance ACID and BASE principles?
Many modern databases implement a hybrid approach, offering strong consistency where needed and eventual consistency where scalability is prioritized.
- NewSQL databases like Google Spanner, CockroachDB, and YugabyteDB use distributed architectures while maintaining ACID compliance.
- MongoDB and Cassandra primarily follow BASE but offer transaction support for multi-document operations.
- Databases like PostgreSQL support logical replication and multi-master setups to offer high availability without fully sacrificing ACID guarantees.
What are the trade-offs between ACID transactions and event-driven architectures?
In event-driven architectures, microservices often communicate through event logs (e.g., Kafka) rather than strict ACID transactions. The trade-offs include:
- Scalability: Event-driven systems scale horizontally, while ACID transactions introduce contention and locking.
- Consistency: ACID guarantees strong consistency, whereas event-driven systems favor eventual consistency.
- Complexity: Event-driven architectures require idempotency, message deduplication, and exactly-once processing to prevent issues that ACID transactions naturally handle.
- Resilience: ACID ensures durability through transactional logs, while event-driven systems maintain reliability through mechanisms like event sourcing and saga patterns.