Track
With businesses increasingly migrating to the cloud, security has become a top priority. Amazon Web Services (AWS) provides a highly secure cloud infrastructure, but securing your AWS environment is a shared responsibility.
In this guide, we’ll explore AWS security best practices—from managing identities and permissions to automating compliance and incident response. Whether you're an AWS architect, security engineer, or business leader, these best practices will help you protect your cloud environment effectively.
Understanding AWS Cloud Security
It's important to first understand what AWS cloud security really means and how it differs from traditional on-premise security models.
Defining AWS cloud security
AWS is considered to be the most secure worldwide cloud infrastructure for developing, migrating, and managing workloads and applications. This is backed by its millions of customers, including the most security-conscious industries like government, healthcare, and finance.
Unlike traditional IT security, where organizations control on-prem infrastructure, cloud security operates in a dynamic, distributed, and scalable environment.
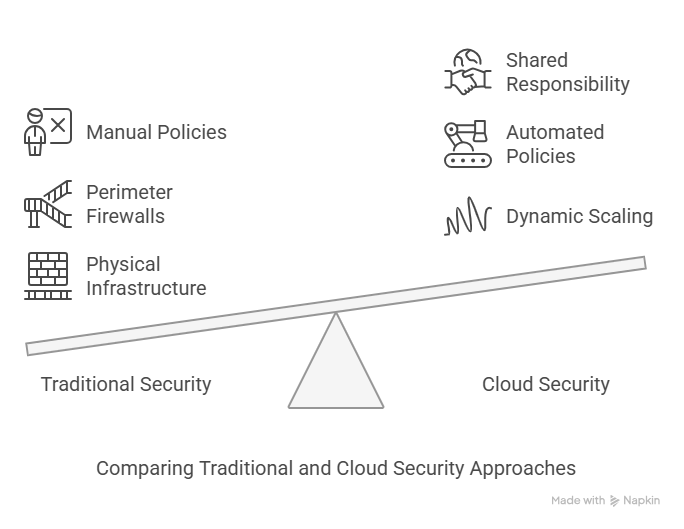
Comparing Traditional and Cloud Security Approaches. Source: Image by Napkin AI
Shared responsibility model
AWS follows what is called a shared responsibility model, which means security is a joint effort between AWS and its customers. In simple words, AWS is responsible for "security of the cloud", whereas the customer is responsible for "security in the cloud." What this means is that being a provider, AWS is responsible for all the physical infrastructure and on top of it, whatever we are adding in the cloud as a customer, we are responsible for that.
AWS takes responsibility for managing and securing the underlying infrastructure including hardware, software, networking, and physical security of the facility. On the other hand, customers are responsible for managing the guest operating system, application software, and the configuration of AWS-provided security group firewalls.
The customer's responsibilities vary depending on the specific AWS services used and the integration into the IT environment, as well as you also need to understand relevant laws and compliance regulations.
Some common misconceptions:
- It is a common misconception that AWS takes care of everything. Because it is the responsibility of the customer to configure IAM policies, security groups, and encrypt sensitive data.
- Another common misconception is that using the default settings is safe. Default configurations often lack proper access controls and logging; and therefore needs to be dealt with care.
Our AWS Security and Cost Management Concepts course is going to be an important resource to help you simplify the complexities of AWS security (with an eye towards expenses).
Unique Challenges in AWS Environments
AWS environments offer speed and scalability, but they also introduce a new set of challenges.
Cloud asset management
AWS resources are created and destroyed rapidly, making asset management complex. For example, resources like EC2 instances, S3 buckets, and Lambda functions can be created and decommissioned in seconds. While this scalability is a huge advantage, it also makes it challenging to maintain an accurate inventory of your assets. Without proper tracking, you might lose sight of what’s running—and what’s vulnerable.
In AWS, instances can scale up or down on their own, and serverless functions (like AWS Lambda) only run when needed. This flexibility is great, but it also creates security risks because unused resources are easy targets for attack.
If you spin up a server or storage and forget about it, hackers can exploit it. The other risk is that without an up-to-date inventory, security checks become guesswork because there is no real-time tracking.
Then what is the fix? It is to use AWS Config to monitor your resources and AWS Systems Manager to keep everything organized. These tools help you track what’s running so nothing slips through the cracks.
Visibility across hybrid/multi-cloud environments
Many organizations use a mix of on-premises infrastructure, AWS, and other cloud providers like Azure. This hybrid or multi-cloud setup can create blind spots, making it harder to monitor and secure all your assets consistently.
The fix is to implement AWS Security Hub for centralized security monitoring. You can also use SIEM solutions like Splunk or AWS GuardDuty to correlate security events across environments.
Dynamic vulnerability management
In the cloud, security threats move fast. Unlike traditional servers that stay the same for months, cloud environments change constantly. For example, new servers may spin up, configuration changes could happen, and vulnerabilities can appear out of nowhere.
Studies like MITRE’s Project Lorelei show that attackers probe new cloud servers within minutes of deployment, making continuous monitoring non-negotiable. Imagine deploying a new database and, before you even finish setting it up, automated bots are already trying to break in.
Continuous monitoring tools (like AWS GuardDuty or third-party scanners) act like 24/7 security guards, spotting suspicious activity the second it happens. You could also use AWS Inspector to scan workloads for vulnerabilities, enable AWS Shield to protect against DDoS attacks, and automate patching using AWS Systems Manager Patch Manager.
Key AWS Security Best Practices
Here are some layered, proactive strategies you should consider:
Take a proactive security posture
Before diving into AWS, take the time to plan your security strategy. Use frameworks like the AWS Well-Architected Framework and CIS Benchmarks to guide your approach. A proactive security posture will save you from headaches down the road.
Follow the AWS well-architected framework
The AWS Well-Architected Framework for security best practices provides a consistent approach for customers and partners to evaluate architectures and implement scalable designs. The framework is built around the six-pillars.

AWS Well-Architected Pillars. Source: Image by Author
Apply CIS benchmarks
The Center for Internet Security (CIS) AWS Foundations Benchmark serves as a set of security configuration best practices for AWS. These are like a security checklist guide for everything from IAM policies to S3 bucket permissions. But benchmarks alone aren’t enough—you need to enforce them. Tools like AWS Security Hub or Prowler (an open-source CIS scanner) automatically check your environment against CIS rules and flag gaps.
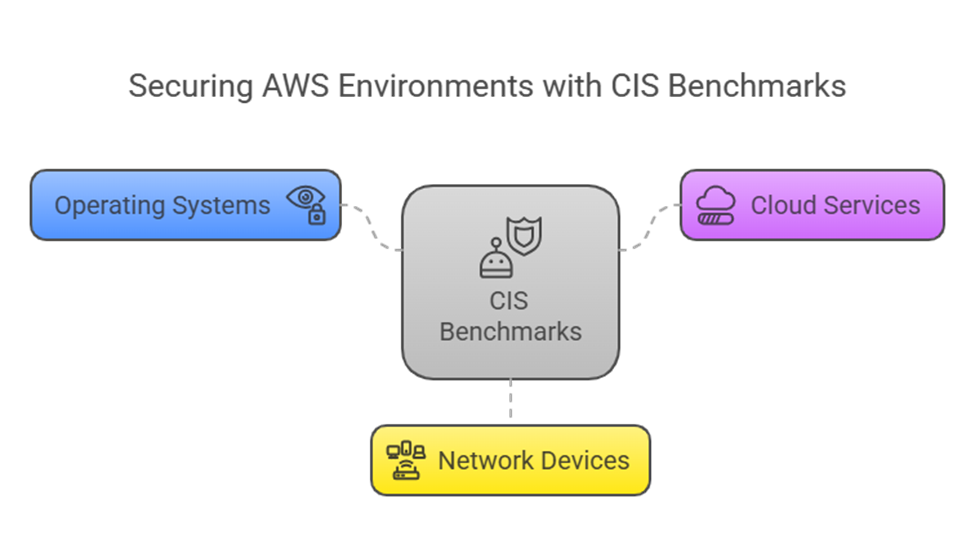
CIS Benchmarks to secure AWS Environments: Source of Image: Napkin AI
Strengthen Identity and Access Management
AWS IAM is critical for controlling access. Misconfigured IAM permissions are a major security risk. IAM is the web service that assists you in safely managing and controlling access to AWS resources. You can regulate which AWS resources users can access by managing permissions with IAM. IAM is used to manage who is allowed (has permissions) and authenticated (signed in) to use resources.
Lock down your AWS environment by applying the principle of least privilege—only grant users the bare minimum permissions they need. Simplify access control with federated SSO and never use the root account for daily tasks. Always enforce strong passwords and MFA, and schedule quarterly audits with regular IAM policy audits and credential rotations. These basic but critical steps drastically reduce your attack surface.
Establish a security baseline
In AWS, a security baseline, implemented through Infrastructure as Code (IaC), establishes a safe, scalable, and uniform basis for your cloud architecture, guaranteeing security and compliance from the onset. By automating infrastructure provisioning and maintenance, IaC solutions such as AWS CloudFormation and Terraform enable you to codify security measures and implement them consistently.
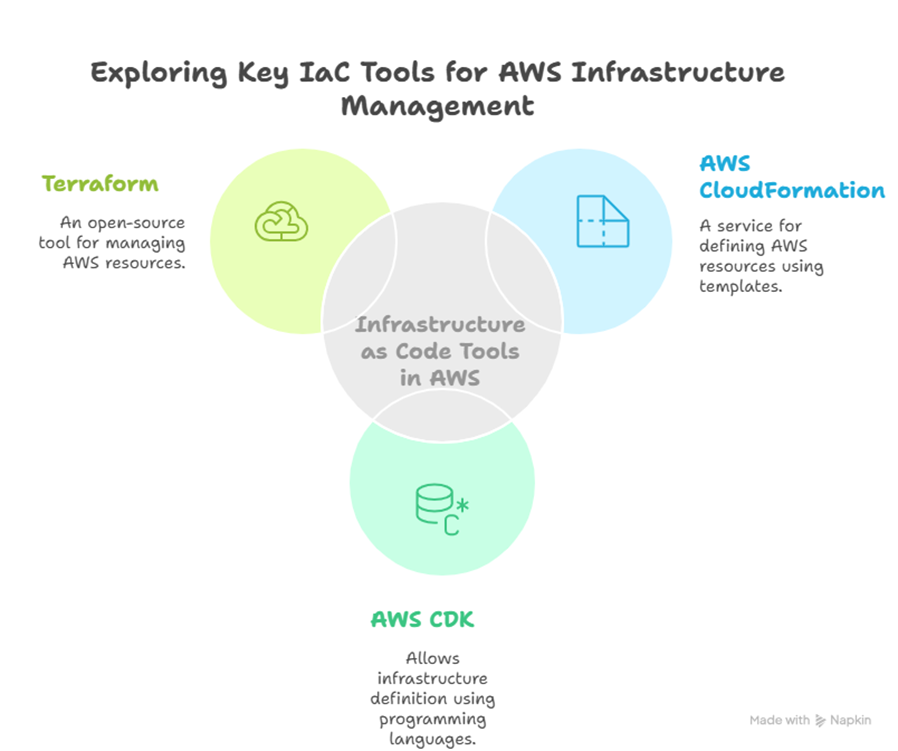
Security Baseline and Infrastructure as Code (IaC). Source: Image by Napkin AI
By automating infrastructure provisioning and maintenance, these IaC tools enable customers to codify and implement security measures consistently.
Set up logging and monitoring
It is almost impossible to identify security breaches without adequate logging. Some of the steps that could be taken are:
- Configure DNS logging to track domain requests,
- VPC Flow Logs to keep an eye on network traffic, and
- AWS CloudTrail to record API calls.
As best practices, integrate these logs with AWS GuardDuty or a SIEM (Security Information and Event Management) system for real-time threat detection.
Manage vulnerabilities and patch systems
Keeping your AWS environment secure requires staying on top of vulnerabilities before attackers can exploit them. It’s not that difficult with AWS Inspector, your automatic security scanner that continuously scans for vulnerabilities across EC2 instances, containers, and apps, keeping you ahead of attacks.
The other thing you can do is to adopt immutable infrastructure for bulletproof patching. For instance, you could replace live servers with new instances from updated AMIs rather than repairing them. This reduces the exposure time, maintains consistency, and gets rid of patch problems.
Automate incident detection and response
One of the smartest ways to strengthen your AWS security is by automating to the extent possible. Instead of manually checking if everything is secure, you can use AWS Security Hub to automatically scan your environment for security issues and make sure you're following best practices. If something looks wrong, you don't have to wait for a person to fix it, AWS Lambda can step in and automatically take action, like fixing settings or isolating a risky server.
To handle bigger security incidents, you can set up AWS Step Functions to organize a series of automatic actions. For example, if AWS GuardDuty finds a suspicious IP address trying to break into your system, Lambda can immediately block that IP address using AWS WAF (Web Application Firewall). This all will be done without anyone having to lift a finger. This way, threats are caught and handled much faster than if you had to react manually.
Unify cloud and on-prem security
It can be a challenging task for any business to manage security, if it is using both the cloud services, as well as its own on-premise servers. In such cases, you can utilize solutions like SIEM (Security Information and Event Management) systems and AWS Security Hub to make things easier.
These technologies consolidate all of your security data in one location, allowing you to monitor the state of both your on-premises and cloud systems without overlooking anything crucial.
AWS Security Final Checklist
IAM Best Practices
✔️ Use IAM roles instead of IAM users
✔️ Enforce MFA on all privileged accounts
✔️ Apply the principle of least privilege (PoLP)
Logging & Monitoring
✔️ Enable AWS CloudTrail and GuardDuty
✔️ Monitor VPC Flow Logs and enable log encryption
Data Protection & Encryption
✔️ Encrypt all sensitive data using AWS KMS
✔️ Use S3 bucket policies to prevent public access
Automated Security
✔️ Implement AWS Config and Security Hub
✔️ Use Lambda functions for automated security responses
Conclusion
Securing your AWS environment isn’t a one-time task, it’s an ongoing process. By following these best practices, you can protect your data, applications, and infrastructure from potential threats. Remember, AWS provides the tools, but it’s up to you to use them effectively.
A secure cloud environment not only safeguards your business but also builds trust with your customers and gives you a competitive edge. So, take the time to implement these practices, and you’ll be well on your way to mastering AWS security.
Got questions or need help getting started? We offer tailored solutions to automate and optimize your cloud defenses. Request a demo today to explore how we can help secure your cloud environment at scale.
Training 2 or more people? Check out our Business solutions
Get your team access to the full DataCamp library, with centralized reporting, assignments, projects and more

Seasoned professional in data science, artificial intelligence, analytics, and data strategy.
FAQs
What is the AWS Shared Responsibility Model?
AWS secures the cloud infrastructure, while customers are responsible for securing their data, applications, and configurations inside the cloud.
Why is identity and access management (IAM) so important in AWS?
IAM controls who can access your AWS resources. Setting it up properly protects your accounts from unauthorized access and misuse.
What tools help with logging and monitoring in AWS?
AWS CloudTrail, GuardDuty, and VPC Flow Logs help track activities and detect threats in real time across your AWS environment.
How do I protect my AWS resources against vulnerabilities?
Regularly scan your instances with AWS Inspector, patch systems quickly, and use immutable infrastructure where you redeploy instead of manually patching.
How can I manage both cloud and on-premise security together?
Use AWS Security Hub and SIEM solutions to get a single, unified view of security across your AWS cloud and on-premise environments.