Track
Securing user identities and managing application access has never been more complex, especially as modern apps scale and threats evolve. Throughout my experience as a developer, I've found that robust authentication systems are essential, but building them from scratch can quickly become overwhelming. That’s why I rely on AWS Cognito, a powerful identity and access management platform that simplifies authentication and authorization, integrates effortlessly with other AWS services, and delivers enterprise-grade security right out of the box.
In this guide, I'll share insights into AWS Cognito’s key features, architecture, setup, and advanced security capabilities, helping you build secure, scalable, and user-friendly solutions.
If you are new to AWS Technology and Security Services, consider taking one of our courses, such as AWS Cloud Technology and Services, AI Security and Risk Management, or AI Ethics.
What is AWS Cognito?
I see AWS Cognito as a fundamental shift in how developers approach identity management for modern applications. This fully managed service provides customer identity and access management (CIAM) capabilities that eliminate the need for building authentication systems from scratch.
AWS Cognito serves as a comprehensive identity service that handles user registration, authentication, and authorization for web and mobile applications. It integrates seamlessly with other AWS services while supporting external identity providers, creating a unified authentication experience.
I believe that understanding its architecture becomes crucial for developers building scalable applications that require secure user management, as it directly impacts how users interact with applications and access resources.
Key Benefits of AWS Cognito
In my work with various identity systems, I have seen that the advantages of implementing AWS Cognito extend far beyond basic authentication capabilities. AWS Cognito transforms how organizations approach identity management by providing enterprise-grade solutions without the complexity of traditional systems.
Scalable customer identity and access management (CIAM)
Cognito's secure and scalable nature makes it ideal for customer identity and access management (CIAM), handling millions of users without compromising performance.
The service automatically scales based on demand, ensuring consistent user experiences during traffic spikes or periods of growth. Security features are built-in rather than added as an afterthought, providing robust protection against common authentication vulnerabilities.
Flexible integration and customization
Integration represents another significant advantage, as AWS Cognito supports various application types, including web, mobile, and desktop applications.
The service offers extensive customization options, allowing developers to tailor authentication flows to match specific business requirements. This flexibility extends to branding, user experience design, and integration with existing systems.
Simplified access management across AWS services
AWS Cognito also simplifies access management to AWS services and resources, eliminating the need to maintain multiple authentication systems. Users can authenticate once and gain appropriate access to various AWS services based on their roles and permissions.
Advanced security features enhance the sign-up and sign-in processes through multi-factor authentication, adaptive authentication, and comprehensive threat detection capabilities.
Common Use Cases for AWS Cognito
From my experience on various projects, applications of AWS Cognito demonstrate its versatility across different industries and use cases. Understanding these scenarios helps developers identify optimal implementation strategies.
Engaging customers with flexible authentication
One primary use case is engaging customers through flexible, customized authentication flows. E-commerce platforms use AWS Cognito to create personalized shopping experiences, while content platforms leverage it to manage subscription-based access. The service supports social login integration, allowing users to sign in with existing accounts from providers like Google, Facebook, and others, reducing friction in the registration process.
Managing B2B identities in multi-tenant applications
A second major application I have encountered is managing business-to-business (B2B) identities in multi-tenant applications, which showcases AWS Cognito's enterprise capabilities. Organizations can create separate user pools for different clients while maintaining centralized management. This approach enables white-label solutions where each client maintains their branding and user experience while leveraging shared infrastructure.
Securing machine-to-machine (M2M) authorization
Beyond user authentication, AWS Cognito excels at securing machine-to-machine (M2M) authorization for IoT or microservices architectures, demonstrating its technical flexibility. IoT devices can authenticate and receive temporary credentials to access specific AWS resources, while microservices can validate user tokens to ensure proper authorization. This capability is essential for modern distributed architectures where multiple services need to verify user identities.
Enabling role-based access to AWS resources
Finally, one of the most powerful use cases I have experienced is providing role-based access to specific AWS resources. AWS Cognito integrates seamlessly with the broader AWS ecosystem, allowing users to receive different levels of access to services like S3 buckets, Lambda functions, and more, based on their roles and attributes. This enables the implementation of sophisticated, fine-grained authorization schemes.
Understanding AWS Cognito Architecture
The architecture of AWS Cognito revolves around two primary components that work together to provide comprehensive identity management. In my experience, understanding these architectural elements is essential for effective implementation.
User pools: authentication engine
User pools serve as what I consider the authentication engine within AWS Cognito, handling all aspects of user registration, sign-in, and profile management. They maintain user directories and provide authentication services for applications, supporting multiple authentication methods including traditional username/password combinations, social identity providers, and SAML-based enterprise identity systems.
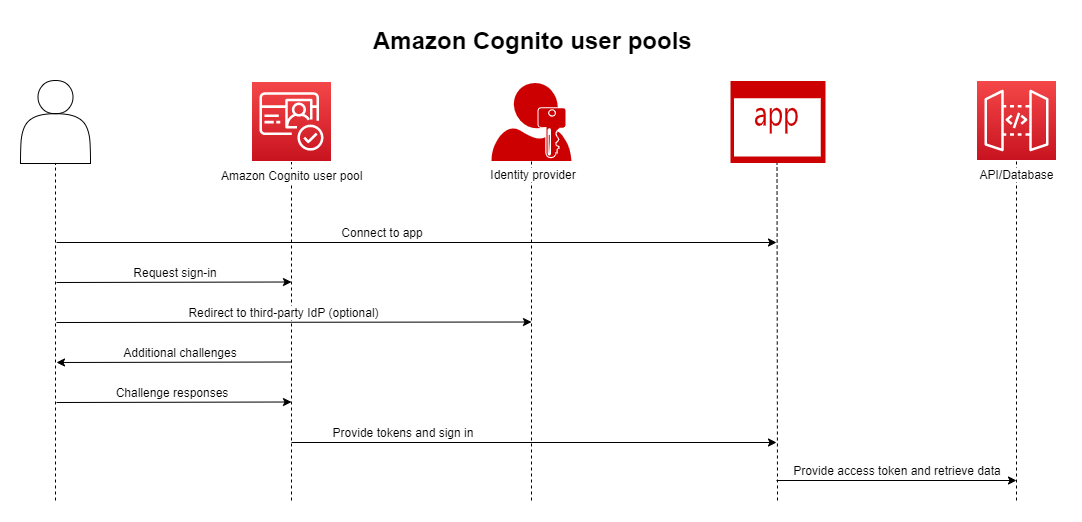
It's worth noting that authentication options extend beyond basic credentials. Social providers such as Google, Facebook, and Amazon can be integrated seamlessly, enabling users to sign in using existing accounts.
For enterprise scenarios, identity integration through SAML and OpenID Connect allows organizations to retain their current identity infrastructure while leveraging AWS Cognito’s capabilities.
Security features in user pools are also key aspects to consider. They include robust multi-factor authentication (MFA), customizable password policies, and account recovery options, among others.
These can be configured to meet organizational policies or regulatory compliance requirements. I always recommend planning attribute schemas before creating user pools, as these schemas define what information is collected and stored about users, affecting both functionality and compliance considerations.
Identity pools: authorization broker
Identity pools function as what I call authorization brokers, translating authenticated user identities into temporary AWS credentials. Unlike user pools, they do not store user information. Instead, they focus on providing controlled access to AWS resources based on verified identities from various sources.

The core function of identity pools is to provide temporary AWS credentials via the AWS Security Token Service (STS). These credentials have limited lifespans and specific permissions, following the principle of least privilege. This approach ensures that users and applications only have access to the resources they need for their current operations.
What I particularly appreciate about identity pools is how they excel at mapping identities to IAM roles through attribute-based rules. This mapping can be based on user attributes, group memberships, or other contextual information. The flexibility of this system allows for sophisticated authorization schemes that can adapt to different user types and access requirements.
User pools vs identity pools: Understanding the differences
The distinction between user pools and identity pools is often a source of confusion. However, understanding their respective roles is critical:
- User pools manage authentication, verifying who the user is. They are ideal for scenarios that require user registration, sign-in workflows, profile management, and integration with external identity providers.
- Identity pools manage authorization, determining what the user can access. They are used to assign AWS resource access to authenticated users, whether those users come from AWS Cognito user pools or external providers.
SDK support also differs between the two. User pools offer rich SDK support for web and mobile applications focused on user management, while identity pools are tightly integrated with AWS SDKs for secure, temporary access to AWS resources.
In many cases, both components are used together. User pools handle authentication, and identity pools facilitate authorization to AWS services.
How AWS Cognito Authentication Works
Understanding the authentication process is essential for developers to implement AWS Cognito effectively and troubleshoot potential issues. The workflow involves several distinct steps designed to ensure secure and efficient user authentication.
Step-by-step authentication process
The typical authentication workflow begins with user registration, where users provide required information and verify their identities through email or SMS confirmation. You can customize this process to include additional verification steps or integration with external identity systems.
Next is the sign-in process, which involves verifying user credentials against the user pool. Upon successful authentication, AWS Cognito issues JSON Web Tokens (JWTs) containing user information. These tokens can be used to access protected resources and services. Tokens have configurable expiration times and can be refreshed to maintain user sessions without requiring reauthentication.
Once users are authenticated, session management becomes crucial to ensure they remain authenticated as they interact with the application. AWS Cognito provides built-in mechanisms for token refresh, session invalidation, and secure logout. Effective session management enhances security while supporting seamless user experiences.
Synchronizing user data with AWS Cognito Sync
For applications requiring cross-device functionality, AWS Cognito Sync enables synchronization of application-related user data across devices and platforms, creating consistent experiences regardless of how users access applications. This capability is particularly valuable for mobile applications where users might switch between devices.
Data synchronization improves user experience by maintaining application state, user preferences, and personalized settings across sessions and devices. Common use cases include synchronizing game progress, application settings, and user-generated content. The service handles conflict resolution when data changes occur on multiple devices simultaneously.
Setting Up Your AWS Cognito Environment
Proper configuration of AWS Cognito components is essential for successful implementation. In this section, I will provide practical guidance for establishing your AWS Cognito environment.
Creating a user pool
Setting up a user pool involves several key configuration decisions that directly impact functionality and security. The process begins with defining basic settings, such as the application type, pool name, and the required attributes for sign-up and sign-in.
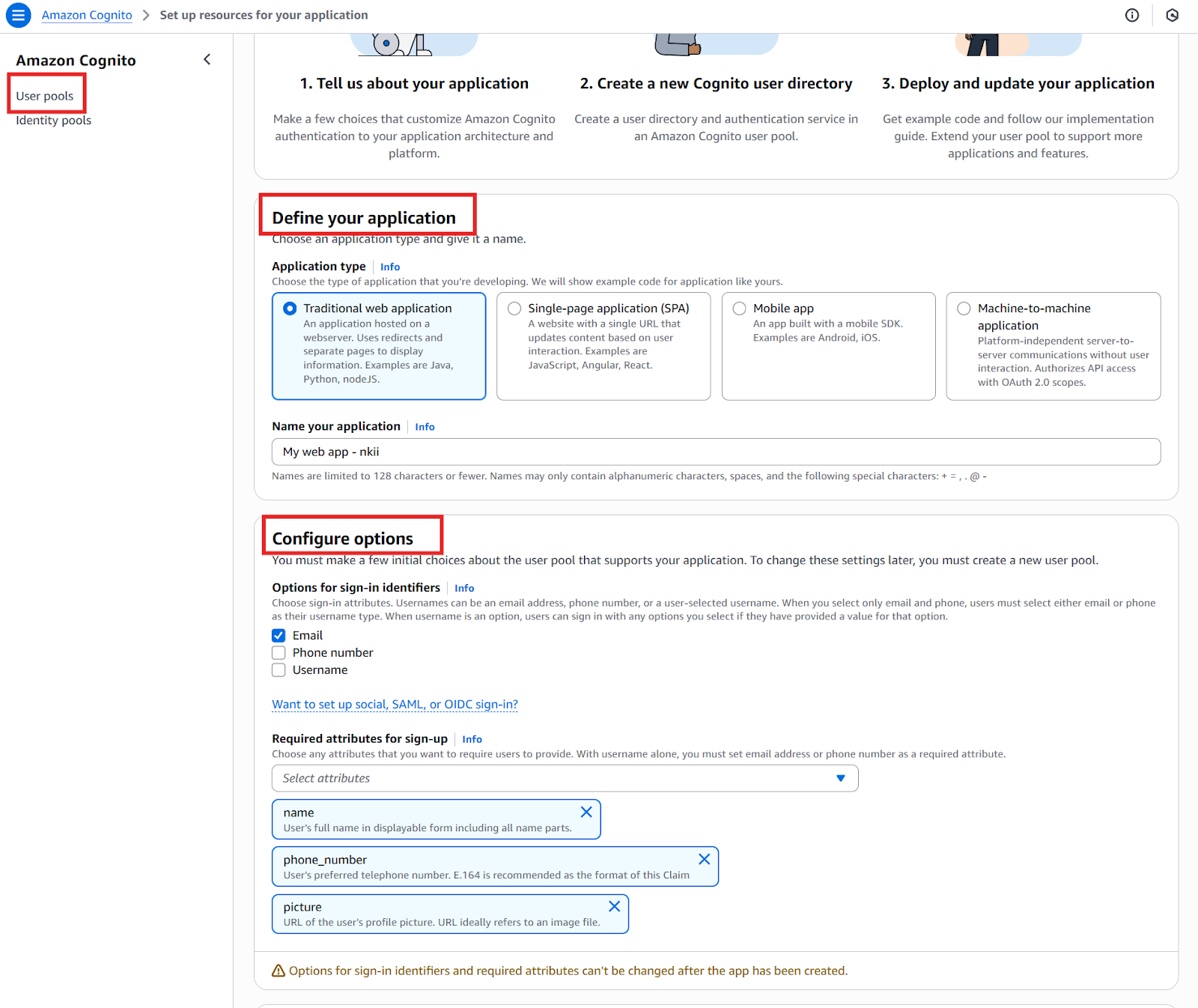
Configuring authentication methods involves selecting supported options for user registration and login. This includes setting password policies, enabling or disabling username/email/phone number as sign-in options, and configuring multi-factor authentication (MFA).
The image below shows the authentication methods section within the user pool. Here, you can configure how your user pool handles email and SMS messaging for users, set password policies, and manage other authentication settings. For instance, you can define password requirements, such as minimum length and character complexity, to enhance security.

The sign-in section provides options for configuring the user sign-in experience. Here, you can enable multi-factor authentication (MFA) to add an extra layer of security and set up device tracking to remember user devices. You can also configure how users can recover their accounts if they forget their password, which is shown under the user account recovery section.
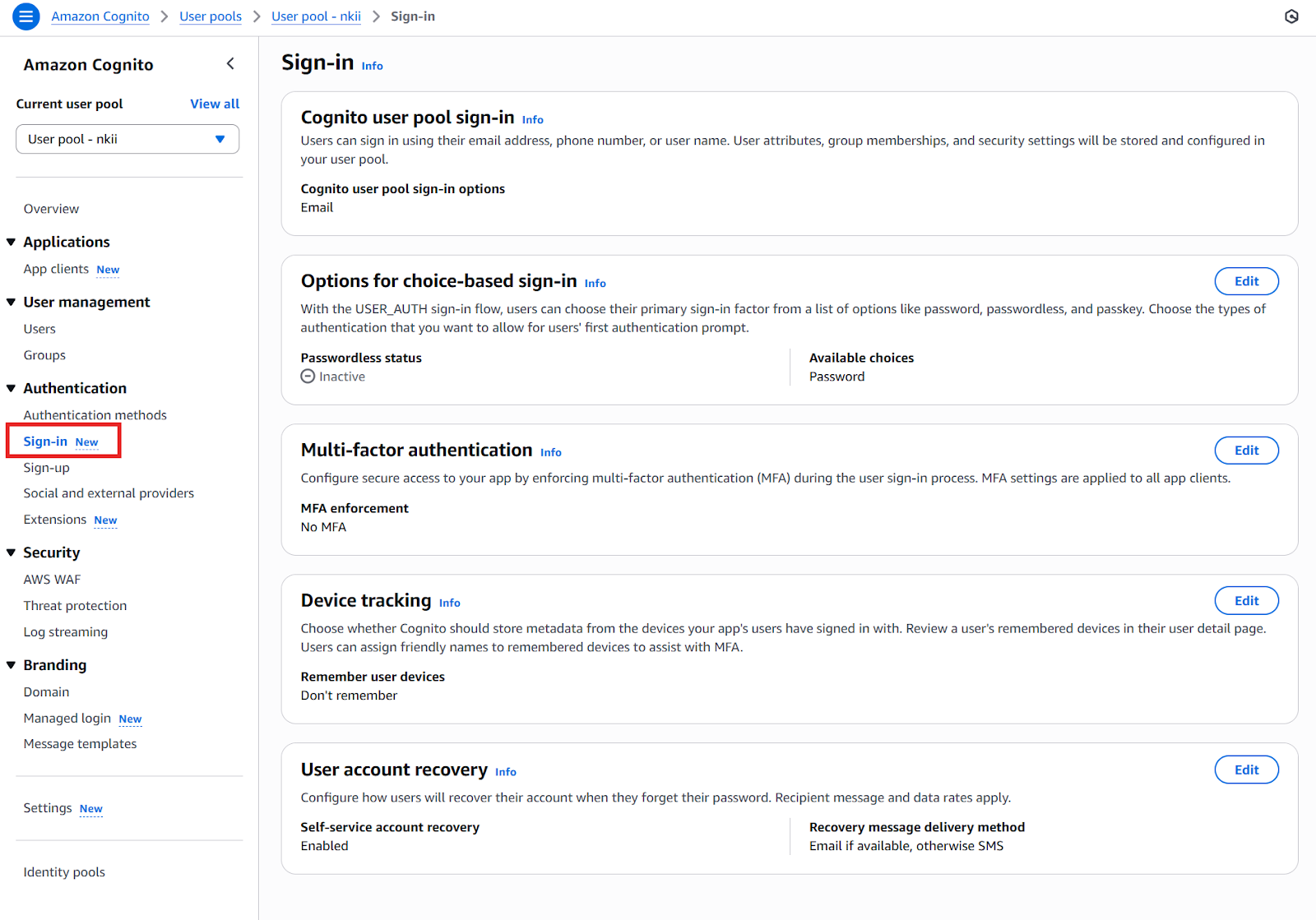
The sign-up section allows you to manage the registration process for new users. As seen in the image, you can choose to have AWS Cognito automatically send messages to verify and confirm user attributes, and you can specify the required attributes for new users, such as picture, phone number, and name. This is where you decide what information is collected from users during sign-up.
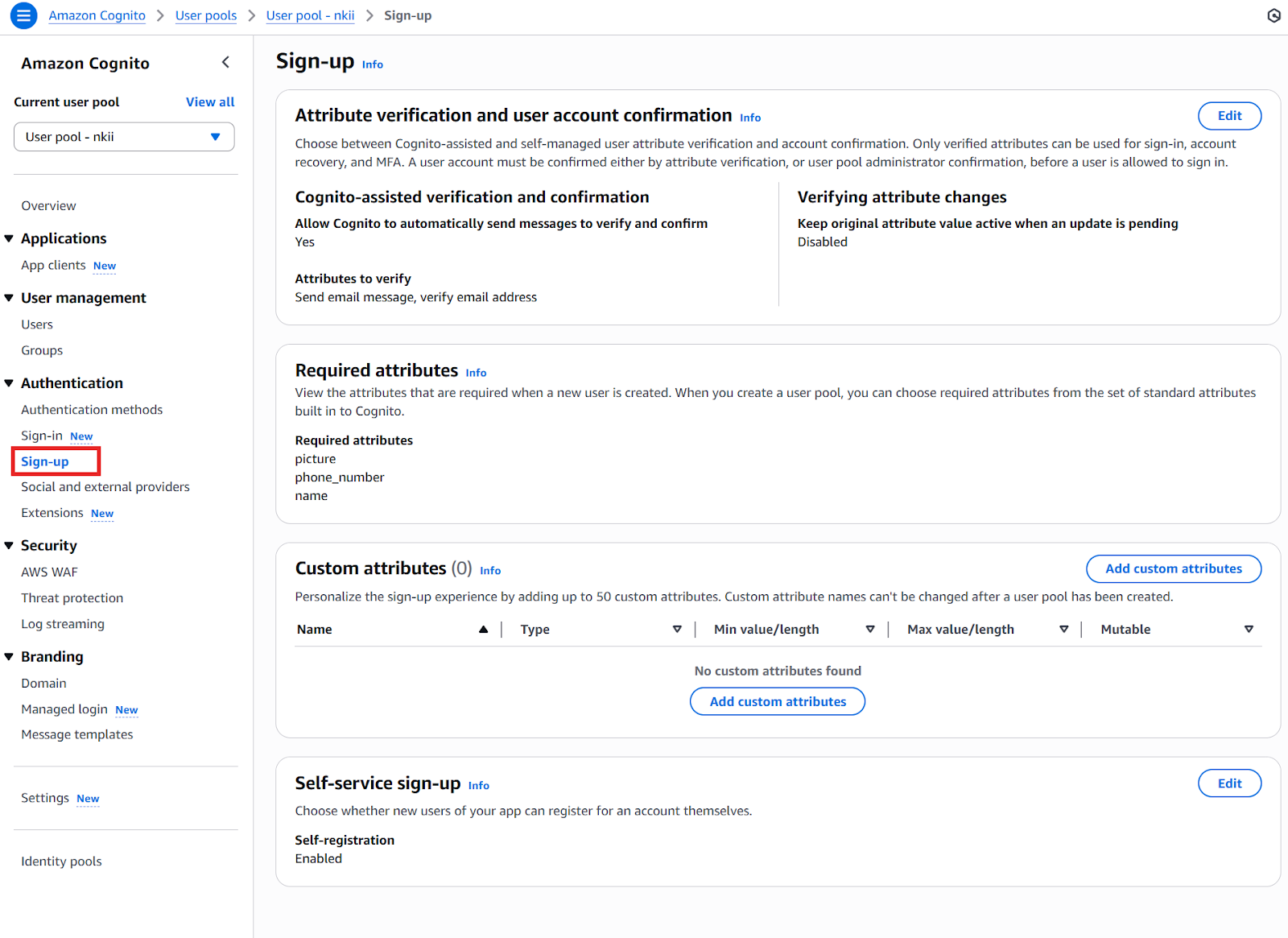
Defining attribute schemas is another critical step. You can choose from standard attributes (e.g., email, phone number) or define custom attributes tailored to your application's specific needs. These attributes influence what user information is collected and how it is used. Additionally, you can customize token claims to include relevant user data used in authorization decisions within your application.
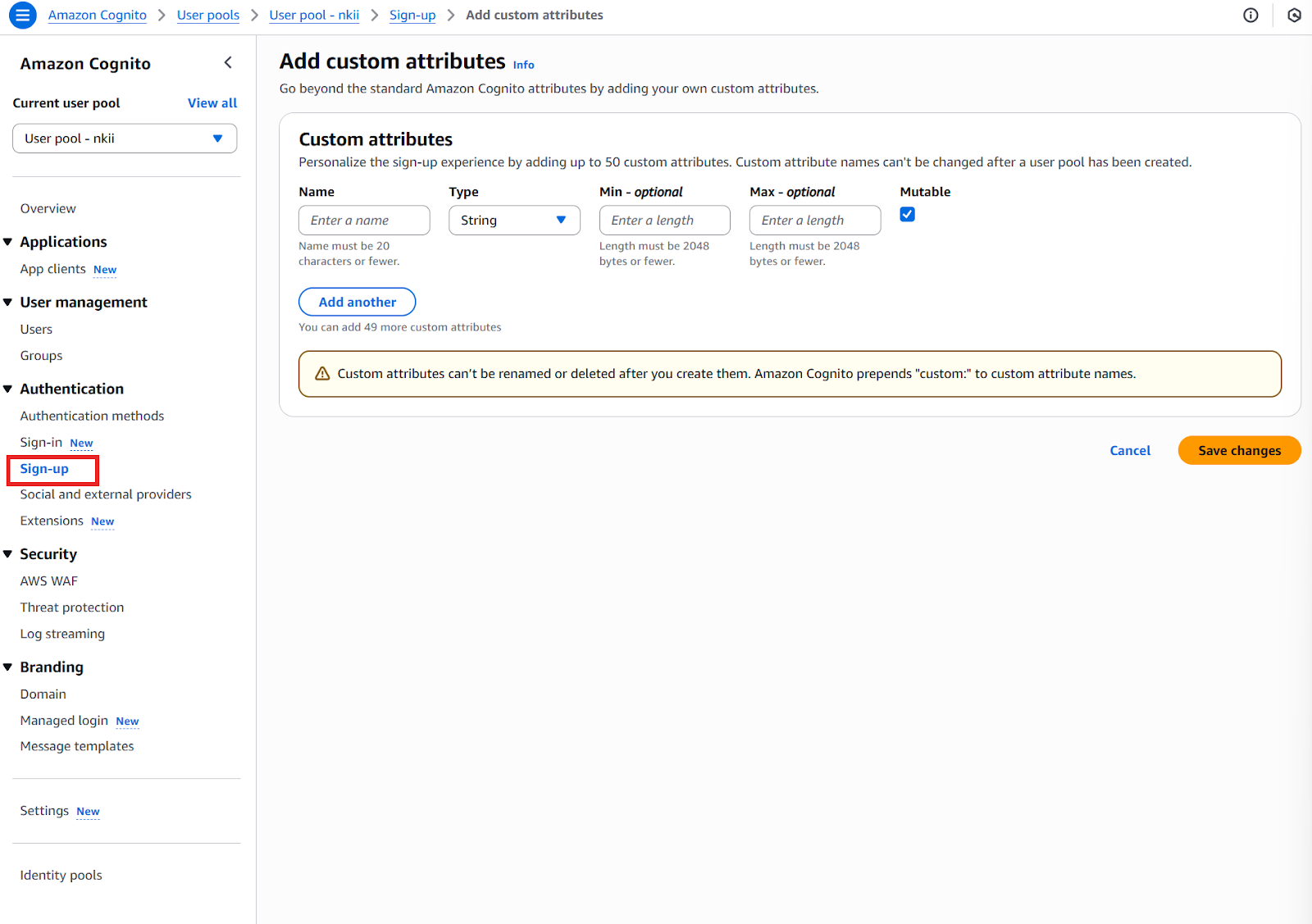
For more advanced customization, AWS Cognito supports Lambda triggers (covered in the next chapter), allowing you to inject business logic into various stages of the authentication workflow. The image displays the options for adding a Lambda trigger, such as for sign-up or custom authentication events. You can use these triggers to filter sign-ups, modify users, or add custom authentication flows.
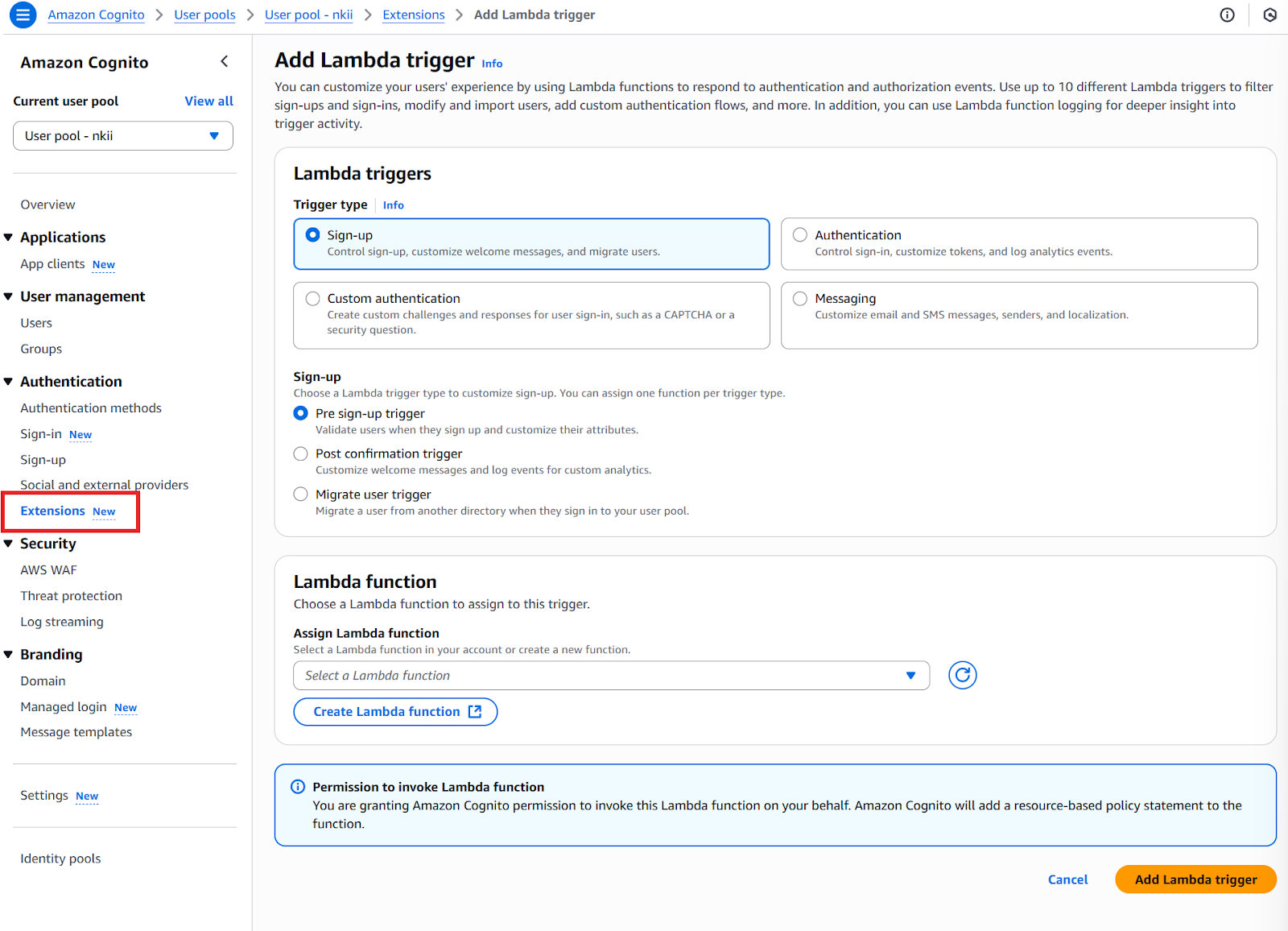
Security settings further enhance your user pool configuration, as illustrated in the image. These include:
- AWS WAF (Web Application Firewall) integration (covered in the next chapter)
- Adaptive authentication to detect and respond to suspicious behavior
- Compromised credentials detection to notify users of potential breaches
- Log streaming to Amazon CloudWatch or other services for auditing and monitoring authentication activity.
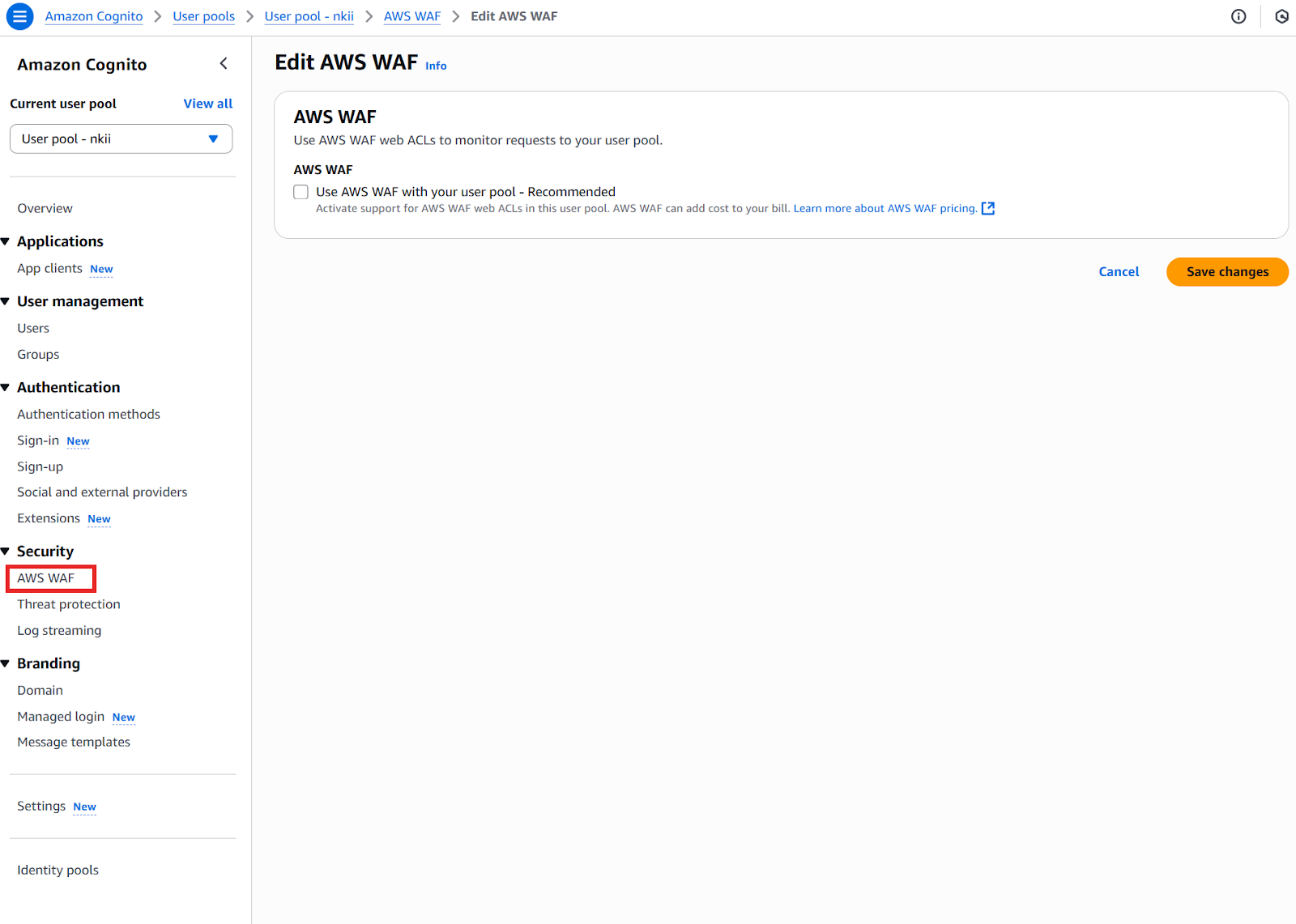
All of these settings should align with your application’s compliance needs, user experience expectations, and threat model.
Configuring an identity pool
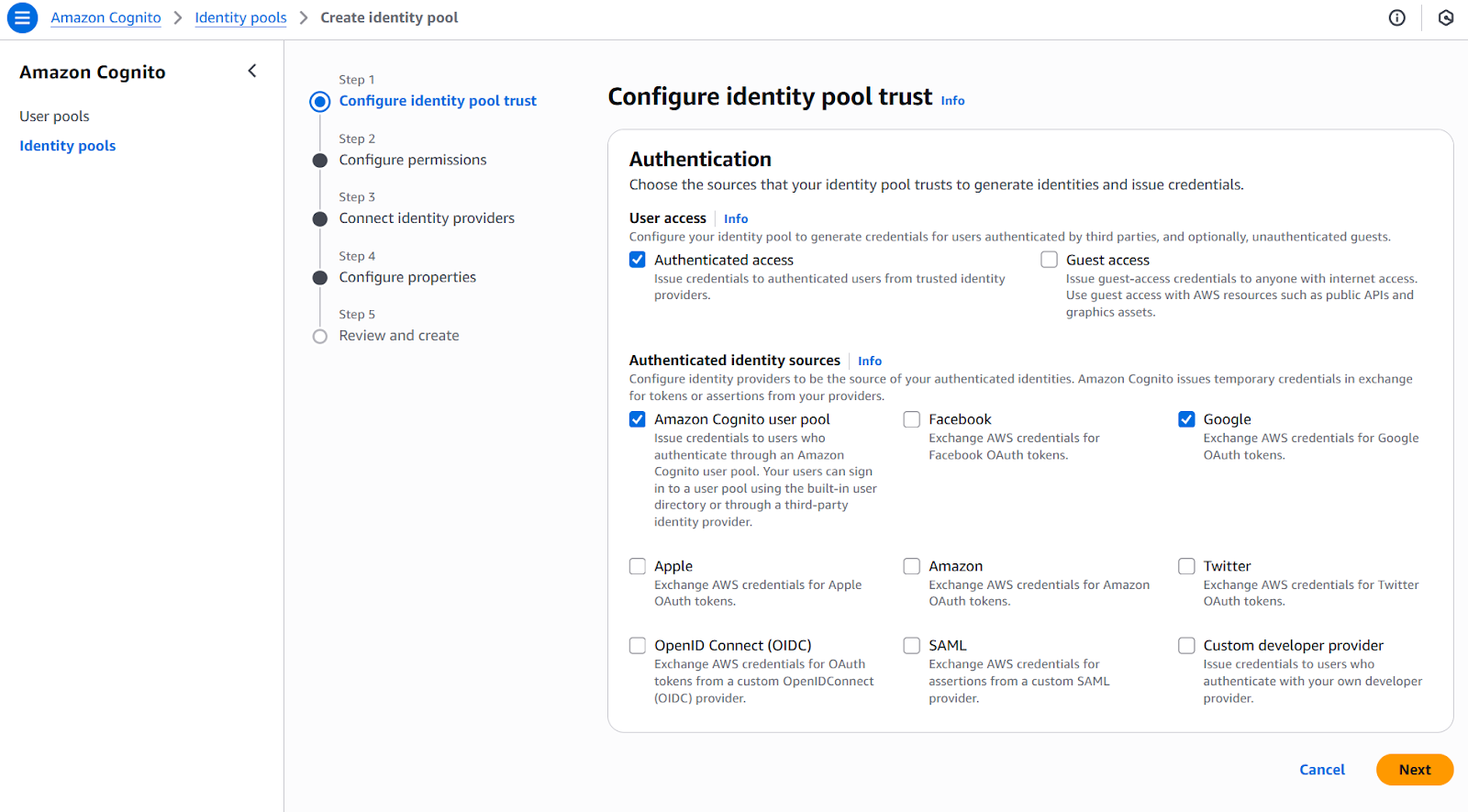
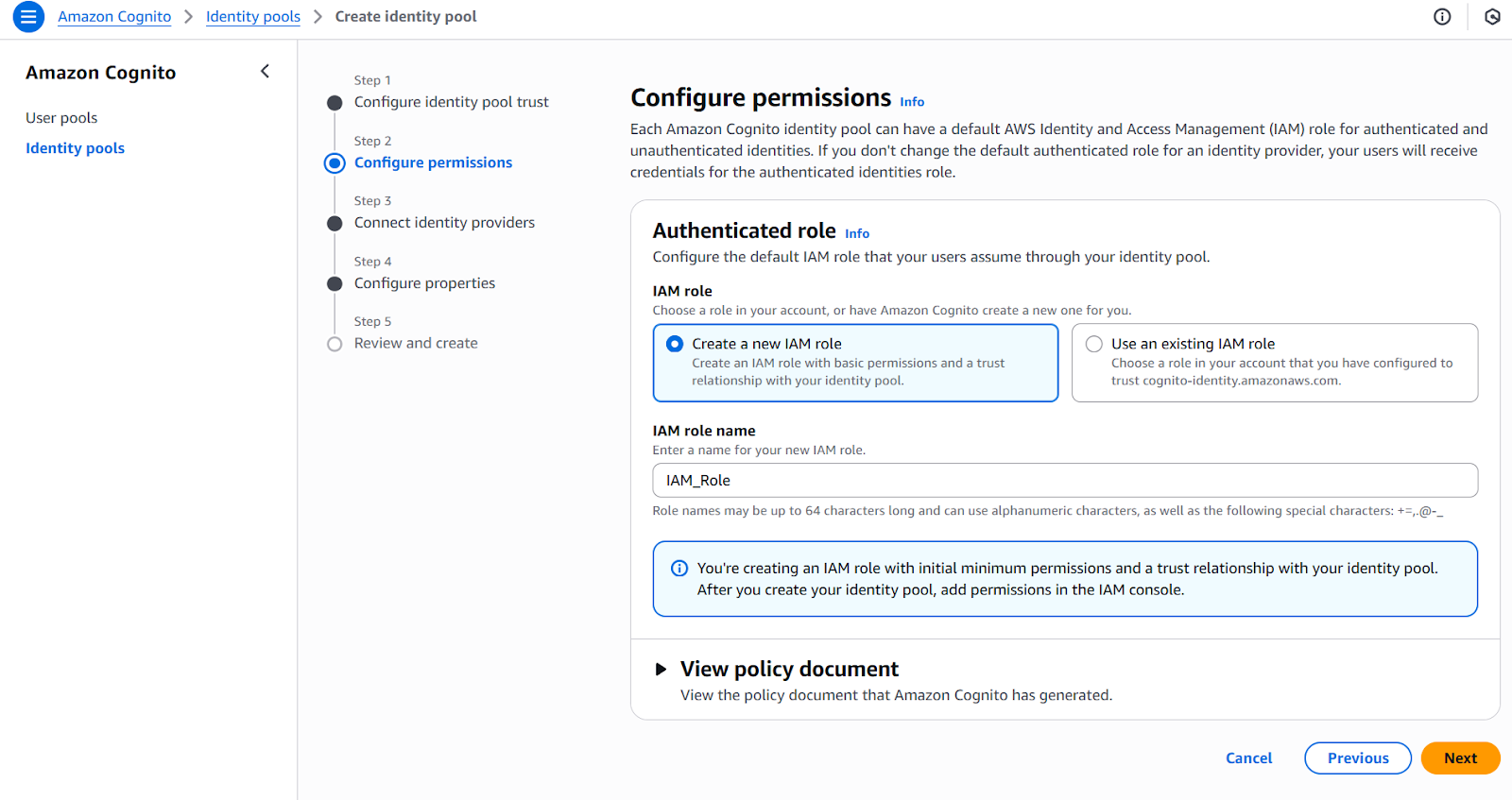
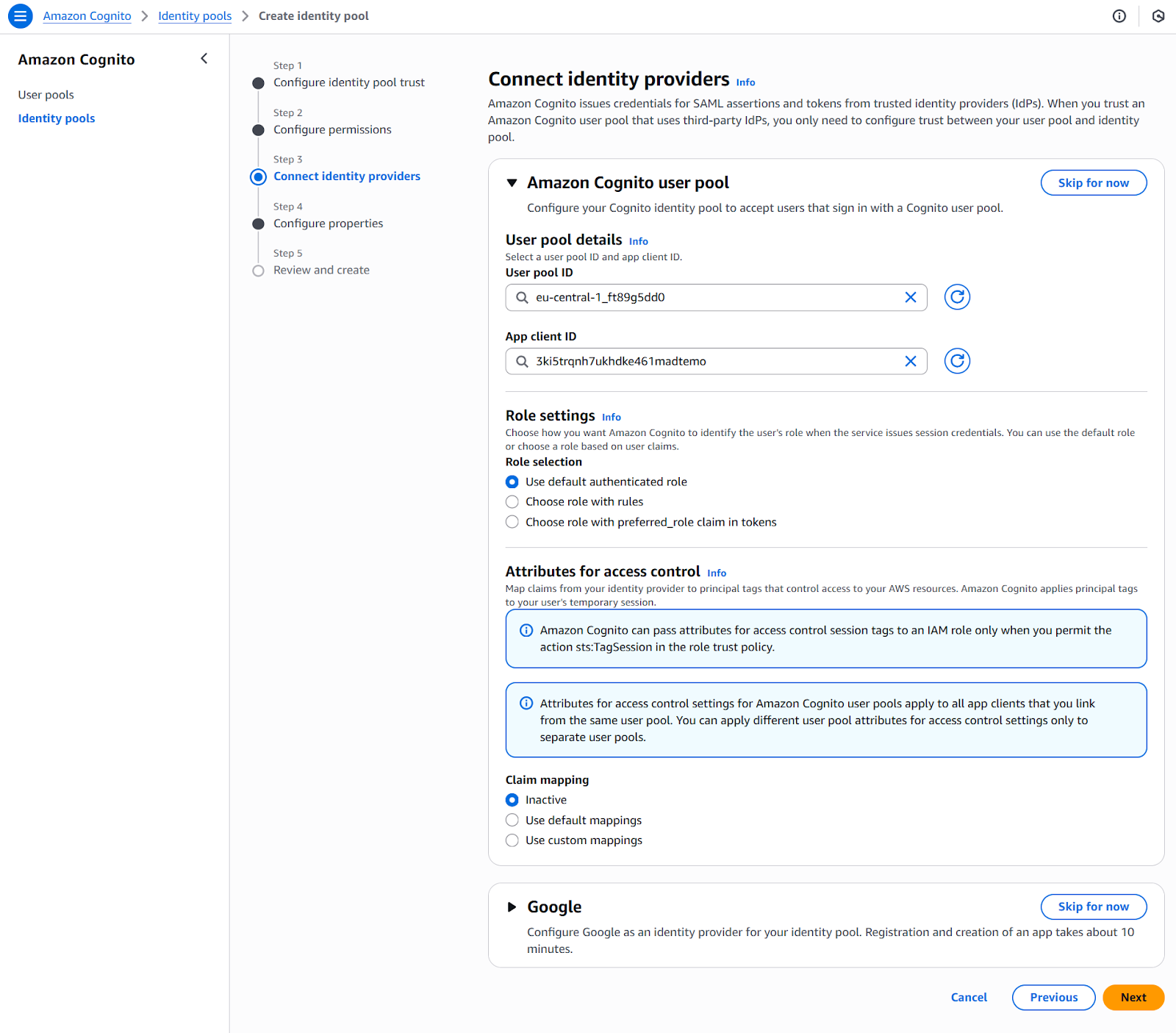
When configuring identity pools, the goal is to provide authenticated users with access to AWS services by issuing temporary AWS credentials via the AWS Security Token Service (STS). Here is my recommended approach for setting up an identity pool:
- Create a new identity pool: Start by creating an identity pool using the AWS Cognito console or AWS CLI. Assign a name and enable access for authenticated users.
- Connect identity providers: Specify the authentication providers that you want to use. These can include:
- AWS Cognito user pools (for users registered through your app)
- Social identity providers (e.g., Google, Facebook, Apple)
- SAML-based enterprise identity providers
- OpenID Connect (OIDC) providers
- Define IAM roles: Set up IAM roles for both authenticated and unauthenticated users. These roles control which AWS resources users can access. Unauthenticated roles can be used for guest access (if needed), while authenticated roles are typically mapped to signed-in users.
By combining user pools and identity pools, you can implement a complete authentication and authorization solution that’s secure, scalable, and deeply integrated with the AWS ecosystem.
Advanced Security and Customization
Beyond basic authentication, AWS Cognito offers advanced security features and customization options that enhance application security and functionality.
Threat mitigation and security features
AWS Cognito includes several built-in mechanisms to help defend against security threats and support compliance:
- AWS WAF (Web Application Firewall) integration protects your application from common web exploits such as SQL injection and cross-site scripting (XSS). WAF rules can be applied to your user pool endpoints to filter malicious requests.
- Compromised credentials detection automatically identifies when user credentials have appeared in known data breaches. When a match is found, AWS Cognito can prompt users to reset their password or block access until the issue is resolved.
- Risk-based authentication evaluates user behavior and contextual signals (such as IP address, device fingerprint, and location) to identify potentially suspicious login attempts. Based on the assessed risk level, AWS Cognito can:
- Prompt for additional verification (e.g., MFA)
- Deny access
- Or allow login with alerts for monitoring
- Audit trails can be created by streaming AWS Cognito logs to Amazon CloudWatch, AWS CloudTrail, or other observability tools. These logs are essential for monitoring authentication activity, supporting compliance audits, and conducting forensic investigations after security incidents.
Together, these security capabilities provide the foundation for enterprise-grade identity protection that scales with your application needs.
Extending functionality with Lambda triggers
AWS Lambda triggers allow developers to inject custom logic into the AWS Cognito authentication and user management workflow. These triggers enhance flexibility by enabling validation, enrichment, integration with external systems, and customization of the user experience during different stages of the authentication lifecycle.
Lambda functions are invoked by AWS Cognito at specific events such as user sign-up, sign-in, token generation, or message delivery. Understanding trigger types, execution context, and error handling is essential for managing and deploying effective functions.
Common use cases for Lambda triggers
- Pre-sign-up validation: Ensure users meet certain conditions (e.g., email domain restrictions, custom fields).
- Post-confirmation actions: Trigger welcome messages or integrate with marketing and CRM systems.Custom authentication flows: Implement multi-step sign-in challenges such as CAPTCHA, passcodes, or security questions.
- User migration: Seamlessly migrate users from external identity providers during their first sign-in.
- Token customization: Inject additional claims into tokens for fine-grained authorization logic.
- Message customization: Personalize email/SMS content or localize messages based on user attributes.
Each trigger point supports a single Lambda function, and some events (like custom authentication) require multiple coordinated triggers. Triggers run within a standard AWS Lambda execution context and must be designed with performance, error handling, and security in mind.
Integration with AWS Services and External Providers
As I highlighted before, AWS Cognito's integration capabilities extend its functionality beyond basic authentication, enabling comprehensive identity solutions that can work together with other AWS services and external providers.
AWS service integration
AWS Cognito can integrate directly with API Gateway to enable secure API access. When a user authenticates through AWS Cognito, the service issues JSON Web Tokens (JWTs) containing user claims. These tokens are used to authorize requests to protected API endpoints, ensuring that only authenticated users with appropriate permissions can access backend services. The user claims embedded in the tokens, such as group memberships or custom attributes, can be evaluated by downstream services to enforce fine-grained access control.
Developers can further enhance integration using the AWS Amplify Framework, which simplifies the process of connecting AWS Cognito with web and mobile applications. Amplify provides ready-to-use authentication components, handles token management automatically, and streamlines backend configuration. This significantly reduces development time while adhering to security best practices, allowing teams to focus more on product features rather than infrastructure.
External identity federation
AWS Cognito also supports integration with external identity providers, enabling social login and enterprise authentication. Applications can allow users to sign in with existing accounts from providers like Google, Facebook, or Apple, as well as enterprise SAML or OpenID Connect (OIDC) systems. This is accomplished by configuring identity providers in the AWS Cognito console and linking them to user pools or identity pools.
Federating external identities through AWS Cognito centralizes user management, even when authentication is handled by third-party systems. This consolidation simplifies auditing, enhances security visibility, and ensures compliance with organizational policies. For end users, the result is a streamlined sign-in experience that eliminates the need to manage multiple credentials across services.
Security and Data Protection
Security in AWS Cognito also goes beyond simple authentication, encompassing comprehensive data protection and adherence to regulatory compliance. This ensures that both user information and application integrity are safeguarded throughout the identity lifecycle.
Data encryption and compliance
User data within AWS Cognito is protected through encryption both at rest and in transit, providing end-to-end security for sensitive information. Data stored in user pools and identity pools is encrypted using AWS-managed keys, while communication between clients and AWS services leverages TLS protocols to secure data exchanges.
AWS Cognito adheres to multiple industry standards and compliance frameworks, including GDPR for data privacy, HIPAA for healthcare information security, and SOC (Service Organization Controls) certifications. These certifications help organizations meet stringent regulatory requirements while managing identities and access control.
Advanced security features
As seen in previous chapters, AWS Cognito offers advanced security features to enhance protection and detect potential threats. Adaptive authentication evaluates risk signals during sign-in attempts and can enforce additional verification steps, such as multi-factor authentication (MFA), when suspicious behavior is detected. Device tracking allows monitoring of user devices to identify unusual or unauthorized access patterns.
For ongoing security monitoring, AWS Cognito integrates with AWS CloudWatch and CloudTrail, providing detailed logs and metrics on authentication events and API usage. These tools enable real-time detection of anomalies and support automated incident response workflows, helping maintain the security posture of your application.
Operational Considerations and Best Practices
Successfully implementing AWS Cognito requires careful attention to operational factors that influence performance, cost efficiency, and long-term maintainability. Understanding these considerations ensures that your identity management system scales reliably with your application needs.
Pricing and tier selection
AWS Cognito offers different pricing tiers that vary in features and capabilities, including factors such as the number of monthly active users and available authentication options.
Choosing the appropriate tier involves assessing your application's user volume, required security features, and expected growth. Selecting the right tier balances cost management with the functionality necessary to support your user base and business requirements effectively.
Global deployment strategies
For applications with a global user base, deploying AWS Cognito across multiple AWS regions can reduce latency and improve availability. However, such deployments require strategies to ensure data consistency and synchronization between regions.
Common approaches that I recommend include using primary-secondary region setups or managing regional user pools with mechanisms for data replication or synchronization. Proper planning addresses challenges such as eventual consistency, failover handling, and compliance with data residency requirements.
Attribute management and migration
Managing user attributes effectively involves anticipating changes to user data schemas and planning migrations carefully. When evolving attribute requirements or migrating from existing identity systems, I always emphasize the importance of designing flexible schema updates that minimize disruptions.
AWS Cognito supports custom attributes and allows for attribute mapping during migrations, enabling smooth transitions. Best practices include thorough testing, versioning of schemas, and clear communication with users to ensure data integrity and seamless user experiences during changes.
Conclusion
From my experience, AWS Cognito simplifies the complexities of modern identity management with a combination of flexibility, scalability, and robust security. By clearly distinguishing between user pools and identity pools, leveraging advanced security capabilities, and integrating seamlessly with other AWS services, I’ve found it significantly streamlines the development of secure and user-friendly applications.
To maximize AWS Cognito’s value, I recommend regularly reviewing security configurations, exploring custom Lambda triggers, and proactively monitoring user access patterns. In my projects, thoughtful planning and ongoing management have consistently been the keys to success.
To keep learning, be sure to check out the following resources:
AWS Cognito FAQs
How does Amazon Cognito handle user data synchronization across different devices?
Cognito Sync synchronizes user data and preferences across devices, maintaining consistent app states and resolving conflicts when data changes on multiple devices.
What are the main differences between user pools and identity pools in Amazon Cognito?
User pools manage user authentication and profile data; identity pools provide temporary AWS credentials for authorized access to AWS resources.
Can you explain the process of setting up custom attributes in Amazon Cognito user pools?
During user pool creation, define custom attributes in the schema to collect additional user data tailored to your app’s needs.
How does Amazon Cognito integrate with social identity providers like Facebook and Google?
Cognito links social providers in the user pool, allowing users to sign in with existing social accounts for seamless authentication.
What are the advanced security features available in Amazon Cognito, and how do they work?
Features include multi-factor authentication, adaptive risk-based authentication, compromised credentials detection, AWS WAF integration, and audit logging for enhanced protection.
As the Founder of Martin Data Solutions and a Freelance Data Scientist, ML and AI Engineer, I bring a diverse portfolio in Regression, Classification, NLP, LLM, RAG, Neural Networks, Ensemble Methods, and Computer Vision.
- Successfully developed several end-to-end ML projects, including data cleaning, analytics, modeling, and deployment on AWS and GCP, delivering impactful and scalable solutions.
- Built interactive and scalable web applications using Streamlit and Gradio for diverse industry use cases.
- Taught and mentored students in data science and analytics, fostering their professional growth through personalized learning approaches.
- Designed course content for retrieval-augmented generation (RAG) applications tailored to enterprise requirements.
- Authored high-impact AI & ML technical blogs, covering topics like MLOps, vector databases, and LLMs, achieving significant engagement.
In each project I take on, I make sure to apply up-to-date practices in software engineering and DevOps, like CI/CD, code linting, formatting, model monitoring, experiment tracking, and robust error handling. I’m committed to delivering complete solutions, turning data insights into practical strategies that help businesses grow and make the most out of data science, machine learning, and AI.
