Course
A healthy economic system relies on trust between buyers and sellers of goods and services. When this trust is broken, the cost of doing business increases. Dishonest actors engage in deceitful transactions to defraud businesses. There are also sophisticated groups of fraudsters targeting specific industries.
In this article, we discuss different types of fraud detected through analytics and the techniques used to detect fraud. We also cover typical fraud detection workflows and the software tools commonly used for fraud analytics.
Explore how AI can impact your organization and how to implement successful AI strategies with our whitepaper, The Learning Leader's Guide to AI Literacy.
What is Fraud Analytics?
Fraud analytics refers to statistical and machine-learning techniques to identify and flag potentially fraudulent transactions, usually in real time.
Discovering fraudulent activity is challenging because:
- Fraudsters use various techniques to mask their transactions as legitimate. So, the seller needs technological and statistical tools to detect potentially fraudulent transactions.
- Fraudulent transactions make up a small percentage of total transactions. Thus, an automated approach is necessary to flag potentially dishonest transactions.
Businesses need to use fraud detection tools that incorporate these features. These tools flag transactions that are highly likely to be fraudulent. Human investigators then manually investigate the flagged transactions and make the final decision.
Detecting potential fraud consists of discovering behavior that:
- Matches with known fraudulent activities.
- Deviates significantly from the normal range.
Empower Your Team with Data Analysis Expertise
Enable data-driven decision-making with DataCamp for Business. Comprehensive courses, assignments, and performance tracking tailored for your team of 2 or more.
Common Types of Fraud Detected Through Analytics
In this section, we explore broad categories of fraudulent transactions, discuss common examples of fraud within each category, and how to use analytics tools to detect and prevent them.
Financial fraud
Financial fraud is perhaps the most well-known and widespread form of fraud. The victims are typically financial institutions and their customers. The culprits are usually fraudsters pretending to be either customers or representatives of financial institutions.
Credit card fraud is the unauthorized use of a card to purchase goods or withdraw money at an ATM. In most cases, this is done using stolen card details. Fraud analytics can help detect card fraud by looking for common patterns like:
- Sudden spikes in the frequency and volume of transactions.
- Successive transactions at multiple locations.
Identity theft happens when someone’s personal information (like bank account numbers, government-issued ID numbers, email passwords, etc.) gets stolen. This information can be used to impersonate the individual to take out loans, open overdraft accounts, and engage in other large financial transactions. Fraud analytics helps in such situations by flagging suspicious behavior like:
- Opening multiple accounts in a short time.
- Deviating from the individual’s known past behavior.
Payment fraud is the use of deceptive means to convince an individual or a business to make a payment for something they are not purchasing. It includes:
- Sending fake invoices to companies.
- Sending fake multifactor authentication messages to confirm a pending payment.
- Impersonating bank staff to extract confidential account-related information.
Analytics can help with payment fraud by monitoring and flagging transactions that:
- Deviate significantly from the account’s usual behavior and payment activity.
- Originate from suspicious IP addresses and device IDs.
Insurance fraud
Insurance fraud includes claiming large payouts for minor incidents and paying small premiums for risky policies. The victim is typically the insurance company, while the culprits pretend to be customers or insurance agents.
Fraudulent claims are about accidents that never happened. To detect such claims, analytics tools:
- Cross-check reported incidents, such as a natural calamity or a road accident, with other sources to verify the truthfulness of the report.
- Analyze patterns in claims made by specific individuals or at particular locations.
Inflated claims exaggerate the damage incurred and the claimed insurance payout in minor incidents. Fraud analytics tools can help with mitigating inflated claims by:
- Estimating typical claim amounts for various accident types based on historical data.
- Matching the reported accident to typical claim amounts for that type of accident.
Insurance surveyors manually verify potentially inflated claims.
Premium evasion involves giving false information to the insurance company to artificially reduce the risk profile and pay lower premiums for a particular policy. Fraud analytics tools can help to:
- Validate the information provided in the policy application against other sources.
- Detect common patterns used in premium evasion. For example, if a vehicle model commonly used for commercial activities is insured for personal use, analytics tools flag it for further investigation.
Fake policies are counterfeit policies created and sold by scammers pretending to be insurance agents. The customer discovers it when they go to raise a claim. Fraud analytics software detects fake policies by:
- Cross-checking the policy details stored in the system with those presented by the customer.
Insurance companies also have a duty to society to identify patterns of fake policies issued in their name. Presenting these analyses to law enforcement helps to catch fake policy rackets.
Healthcare fraud
Healthcare fraud can happen in any part of the healthcare system, including public health insurers. The victim is the payer, who can be one or more of various groups:
- The patient
- The patient’s employer in a co-pay scheme
- The government in publicly funded healthcare systems
- The insurance company
The culprits are often healthcare service providers or patients. Healthcare fraud is typically committed through false claims, including billing for services not rendered and upcoding.
Billing for services not rendered refers to charging payers for services (such as tests and treatments) that were not performed on the patient. To detect this kind of fraud, analytics tools can:
- Use pattern recognition to compare invoices with amounts and items typically billed by industry peers for similar complaints.
- Cross-check invoiced services against service logs of the healthcare provider and patient-treatment records.
- Identify providers with track records of unusually high billing amounts and scrutinize their filings.
Upcoding refers to the malpractice of billing for a more expensive service category than was provided. Fraud analytics tools employ various methods to detect upcoding, such as:
- Statistical analysis to compare the ratio of routine tests and expensive tests (or treatments) against industry standards. For example, a provider that mostly bills for extended and few regular checkups is suspect.
- Comparing invoices with patient and hospital records usually contain details of the procedure or test performed.
- Comparing the billed amounts with the provider’s historical data to check for sudden increases in specific upcoded categories.
E-commerce and retail fraud
Many e-commerce sellers are small and medium enterprises that are not necessarily tech-savvy. Thus, the onus lies on e-commerce platforms to detect fraudulent activity and curb it. E-commerce and retail fraud can happen in various forms:
Account takeovers refer to a user losing control of their account to fraudsters who abuse it by making unauthorized purchases. This usually happens due to user error or inattentiveness to security considerations like passwords and phishing scams.
E-commerce platforms can detect account takeover using techniques like:
- Behavioral analysis to check for deviations from typical behavior, like login times, purchase categories, browsing history, etc.
- Anomalous activity (like multiple failed login attempts) combined with changes in account settings (like email IDs and delivery addresses).
Fake returns occur when malicious actors return items different from the purchased item, like ordering an expensive item and returning a counterfeit. It also includes returning used products that cannot be resold. To protect against fake returns, fraud analytics can:
- Analyze return patterns to identify buyers who frequently return items.
- Compare the original purchase to verify that the returned item is the same as the one purchased.
- Ensure that the returned item is in unused condition.
Fraudulent purchases involve unauthorized transactions using stolen or fake payment information and compromised accounts. They can lead to losses for both sellers and unsuspecting buyers. Fraud analytics can help to flag potentially fraudulent purchases by monitoring transactions to identify patterns like:
- Frequent logins from multiple accounts are made using the same IP address.
- Trying different credit card numbers in rapid succession.
- Unusually large purchases, considering the account’s history.
Chargeback fraud involves abusing the credit card’s chargeback policy to claim refunds on legitimate purchases. Fraud analytics can help protect against chargeback fraud by using:
- Pattern recognition to identify users who engage in frequent chargebacks.
- Machine learning to detect suspicious behavior like multiple purchases in rapid succession, especially with new accounts and recently updated payment details.
Techniques Used in Fraud Analytics
Fraud analytics tools use a common range of techniques by adapting them to different contexts, datasets, and behaviors of fraudsters in that domain.
All fraud analytics methods have two key goals:
- Detect and prevent fraud
- Facilitate genuine customers
Anomaly detection
Fraudsters often display significantly different behavior compared to legitimate customers. Anomaly detection helps to identify unusual behaviors that point to potentially fraudulent activity. It encompasses a range of methods:
- Statistical outlier detection helps identify data points significantly different from the rest of the distribution. Suspicious behavior is often indicated by outliers in various metrics, such as:
- The frequency of transactions per hour.
- The number of zip codes where a card is swiped in a day.
- Isolation forests consist of multiple isolation trees. Each isolation tree works as follows:
- Randomly choose an attribute of the data and randomly partition data points based on the value of that attribute.
- For each partition, choose another random attribute and partition it further.
- This process continues iteratively until each data point is isolated into a partition with only that point.
- It is observed that anomalous points with extreme values are isolated (into individual partitions) in fewer iterations than normal data points.
- Local outlier factor is a method of identifying anomalous behavior by calculating the density of points in various areas of the distribution.
- When a customer behavior dataset is represented graphically, it forms dense clusters, each corresponding to a customer group.
- Each data point (customer) in a cluster exhibits similar, but not identical, behavior. It is often observed that fraudulent data also forms a cluster that’s segregated from normal customers’ clusters.
Check out the Anomaly Detection in Python course to further understand this technique.
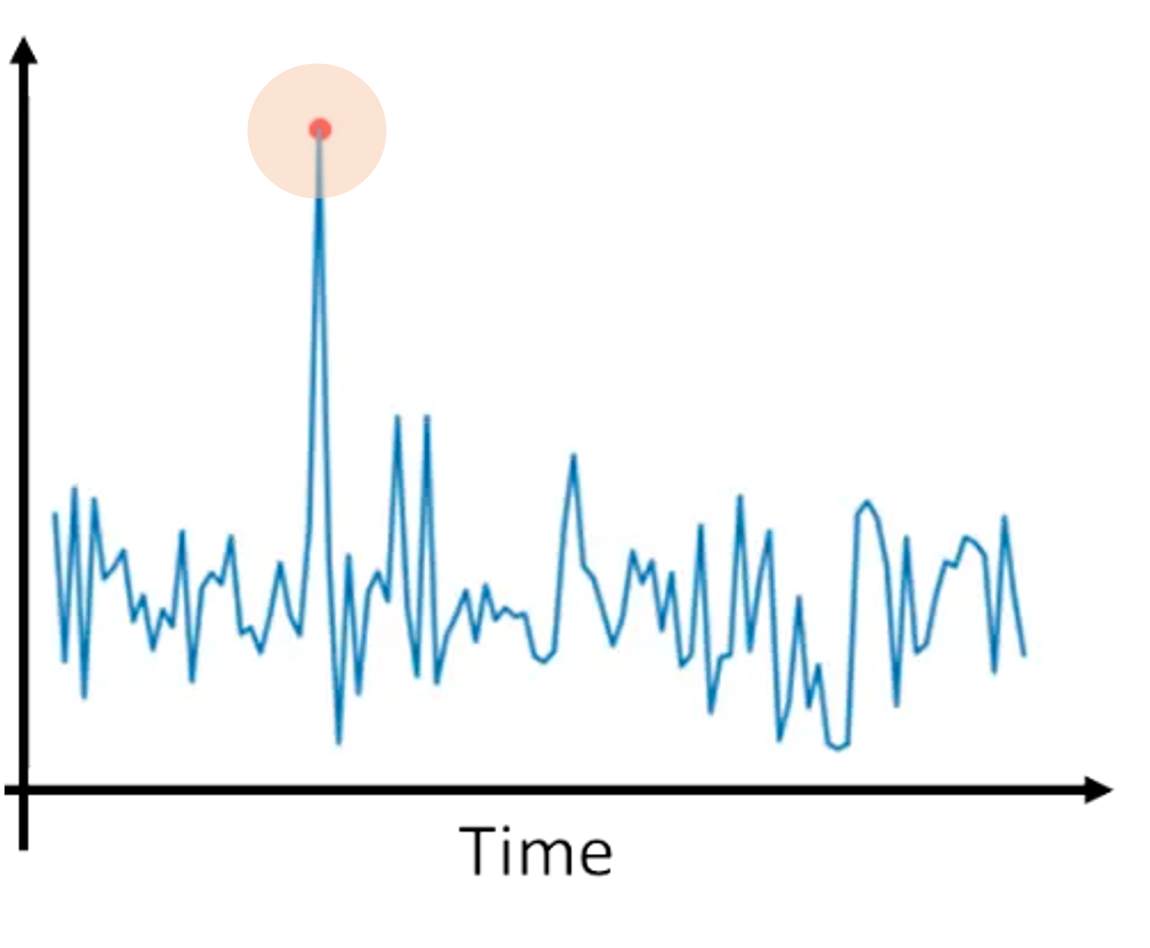
Illustration of anomaly detection. Image source: Understanding AI
Supervised machine learning
Supervised machine learning is a proven method of anomaly detection. Humans label datasets based on known instances of past fraudulent behavior. Machine learning algorithms are then trained on labeled datasets to predict the likelihood of a new transaction being fraudulent.
- Logistic regression predicts the probability that a data point belongs to one of two groups, such as genuine and potentially fraudulent.
- Each point in the training dataset is labeled as either fraudulent or genuine.
- During training, the model learns patterns in the features that point to fraudulent transactions.
- When presented with new data, the model can predict the likelihood of the data point being fraudulent.
- Decision trees recursively split the dataset into subsets. Each node splits data points into two branches according to the values of one particular attribute (such as transaction frequency or monthly transaction volume).
- After a series of such splits, each branch terminates in two leaf nodes - fraudulent and genuine.
- During the training, the model learns the rules for each node to split the dataset.
- The model classifies each new transaction according to these rules and predicts whether it is likely to be fraudulent or genuine.
- Random forests consist of multiple decision trees. A decision tree applies a series of if…else conditions to decide if a transaction is fraudulent. These if…else conditions are based on the features of the dataset.
- Each tree in a random forest is trained independently to use a random subset of features to predict fraudulent transactions.
- The prediction of the forest is based on aggregating the output of all the individual trees.
- This approach avoids the overfitting problem common to decision trees by considering subsets of the feature set.
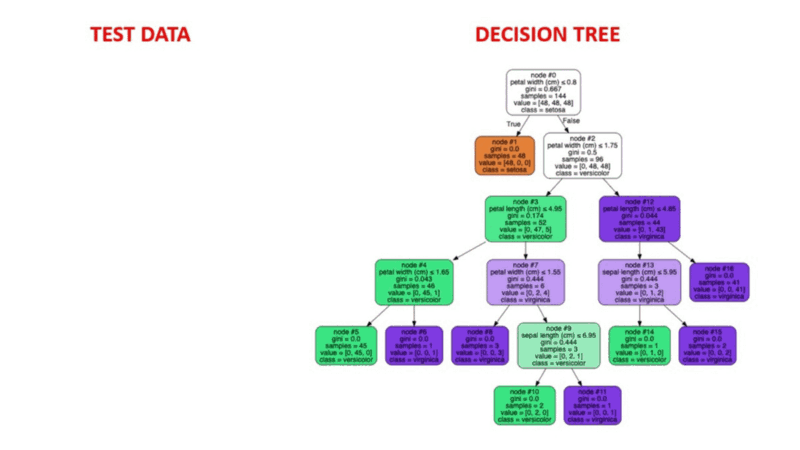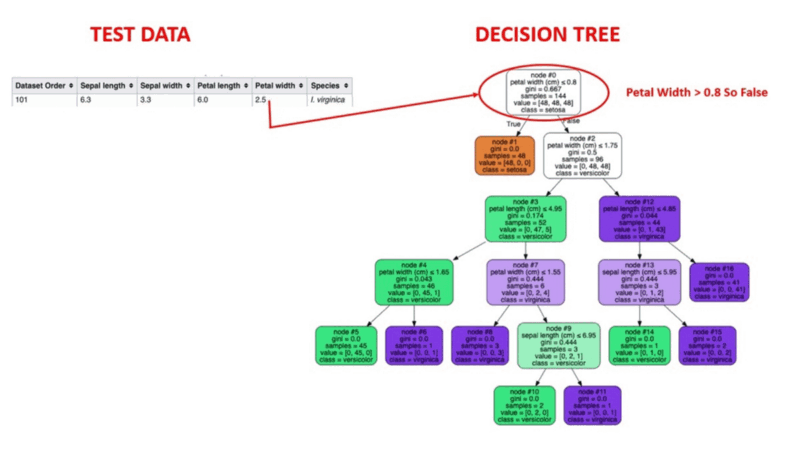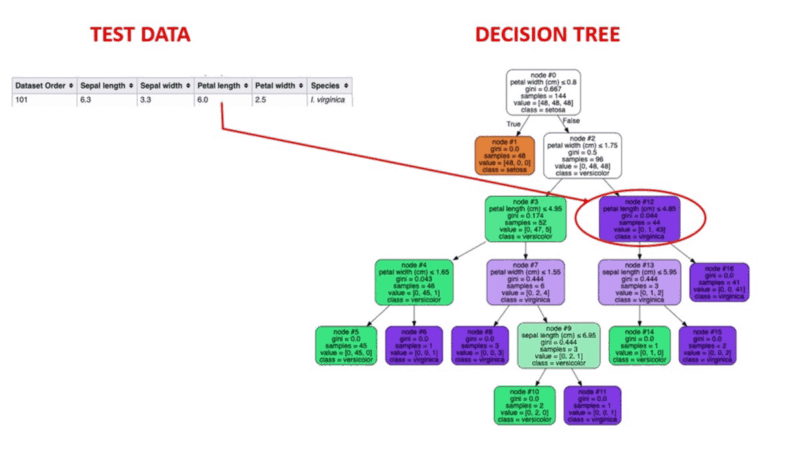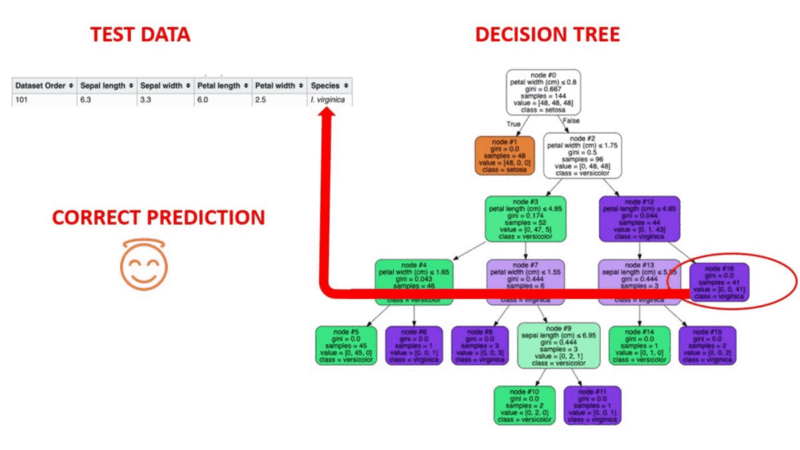
Animated Illustration of how decision trees work. Image source: Supervised Machine Learning
Check the Supervised Machine Learning in Python course track to learn more about these techniques.
Unsupervised machine learning
Supervised machine learning algorithms, which predict based on past behaviors, become less effective as fraudsters adopt new methods.
Unsupervised machine learning is helpful in predicting unknown patterns in the data. The other advantage of unsupervised methods is that you don’t need to spend human resources to label large datasets. The algorithm detects patterns by itself.
- K-means clustering groups the entire dataset of transactions into different clusters based on the values of the data points along with different attributes.
- Data points within each cluster have similar attributes, like transaction frequency. Fraudulent transactions are observed to not fall into any of the other major clusters.
- Visually, they tend to be far removed from the other clusters. Potentially fraudulent transactions can be identified by analyzing these outlier clusters.
- Density-based spatial clustering of applications with noise (DBSCAN) involves representing transaction datasets in a feature space. In this representation, data points segregate into high-density and low-density regions.
- Regions of higher density are considered clusters, and sparse regions are considered outliers.
- Data points that fall in sparse regions are flagged as potentially fraudulent. These are then analyzed for further evidence of suspicious activity.
How clustering works. Image source: Clustering in Machine Learning
Check the Unsupervised Learning in Python to learn more about the mentioned techniques.
Network analysis
Traditional methods of fraud detection by pattern matching for suspicious behavior are effective for individual accounts. However, fraudsters often operate as groups of individuals using a set of devices, email accounts, and physical addresses, making it challenging to track suspicious behavior when that account is considered in isolation.
- Fraud rings are groups of individuals who engage in coordinated attacks. For example, ring members might use ten different devices and IP addresses to make ten successive transactions. Network analysis can detect relationships between various entities to create entity relationship maps and identify fraud rings.
- Entity relationship maps are graph-like structures with nodes representing entities and the edges representing their relationships. Entities can be individuals, accounts, email IDs, device IDs, IP addresses, physical addresses, and more. Relationships between entities denote any commonality or similar behavior, such as:
- Various IP addresses using the same stolen payment details.
- Various accounts placing fraudulent orders to the same physical address.
Check the Introduction to Network Analysis in Python course for a deeper understanding of these techniques.
Text mining and natural language processing (NLP)
Many forms of fraud, like false insurance claims, fake customer reviews, phishing emails, and the like, are based on blocks of text. Analyzing their text content often leads to clues to distinguish genuine customer activity from attempts at fraud.
- Natural language processing (NLP) consists of techniques like sentiment analysis and named entity recognition (NER). NLP is used in applications like:
- Fraudulent insurance claims often contain inconsistencies in the claim description. NLP can identify contradictory statements and unusual language, while NER can point to relationships between places, dates, and people.
- Fake customer reviews are often submitted by various accounts for the same product or by the same account for various products. These reviews tend to contain similar language, which is identifiable using sentiment analysis and tone detection.
- Phishing emails and other hacking attempts based on social engineering often follow similar language patterns designed to extract sensitive information from the recipient. Standard NLP methods are useful for identifying such patterns and warning the recipient.
- Text mining algorithms process large volumes of unstructured text, like emails, claims, and reviews, to detect common occurrences of suspicious language patterns and specific terminologies that are common to fraudulent activity.
- The key assumption behind text mining is that most fraudulent activity falls into a limited number of categories and is executed by a small group of individuals. Thus, identifying commonalities by looking for patterns in the text content is a viable method to flag potential attempts at fraud.
Check the Natural Language Processing in Python skill track for a more in-depth understanding of the subject.
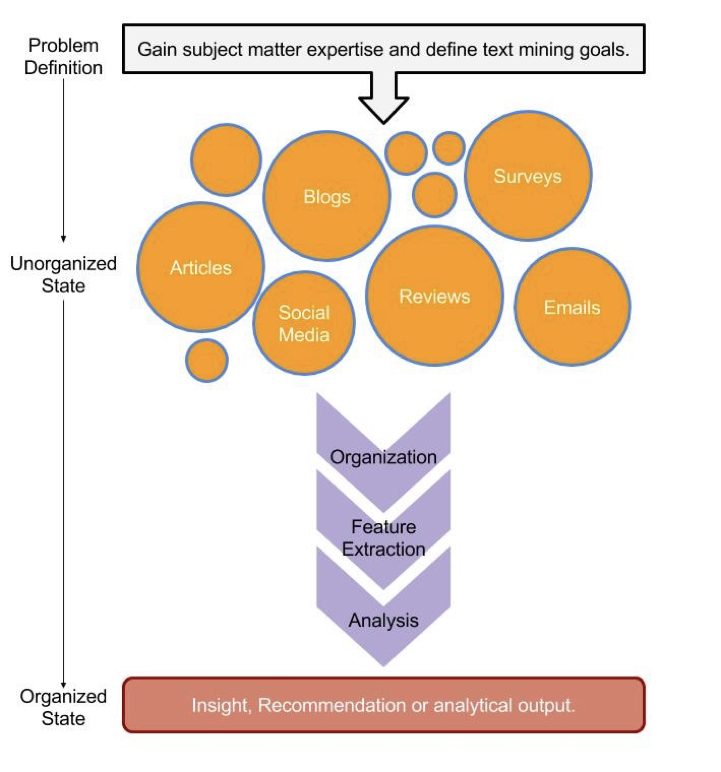
Illustration of the text mining workflow. Image source: Text Mining with Bag-of-Words in R
Fraud Detection Workflow
In this section, we give a high-level overview of the practical principles of implementing fraud detection workflows.
Data collection
All fraud detection algorithms are based on analyzing and identifying patterns observed in large datasets. Thus, high-quality, relevant, and curated datasets like transaction logs and customer profiles are crucial to train these algorithms.
- Transaction logs are used to analyze historical transactions and uncover patterns based on details such as amounts, volumes, frequency, IP addresses, timestamps, and more.
- Customer databases contain addresses, payment details, browsing histories, purchase histories, reviews left, returns, and more.
- Third-party data sources are useful for confirming observations based on internal datasets and enhancing data quality.
Data preprocessing
After collecting data, the next logical step is to use it to train fraud detection models. Raw data is typically unsuitable for training models. Thus, cleaning and normalizing the data before using it as a training dataset is necessary. Data preprocessing, together with feature engineering, covers these steps.
- Data cleaning addresses missing values, wrongly formatted values (for example, numbers formatted as text), duplicate records, wrong values, and more. Leaving such values in the dataset leads to a poorly trained model. Thus, data cleaning is the first step towards ensuring a usable dataset.
- Data normalization involves expressing numerical values on a uniform scale. It can also include translating letter-based ranks to numerical values. It is especially important when data sources are combined to form a larger dataset.
- Feature engineering transforms the available information into more useful forms.
Model training and evaluation
Fraud analytics algorithms are, at their core, built upon machine learning techniques. Historical data is the basis for training machine learning algorithms. After collecting and cleaning the data, the next step is to train the models. During training, the model learns to predict which transactions or user profiles are more likely to be fraudulent.
Besides flagging potentially fraudulent behavior, it is equally important not to obstruct regular users. A false positive is when the model flags a genuine transaction as fraudulent. Minimizing false positives is important to maintain a good customer experience. To ensure this, the trained model is evaluated using various metrics.
Real-time fraud detection
After committing fraud, it becomes increasingly challenging to recover the stolen funds or goods from the fraudster. Thus, the goal is to detect and prevent fraud in real time before the transaction is executed. Integrating fraud analytics into the transaction processing pipeline enables real-time detection. There are two ways of doing this:
- Streaming data from the transaction pipeline to a real-time fraud analytics system: Event streaming tools like Apache Kafka enable transmitting real-time transaction data into fraud analytics systems. The real-time fraud analytics platform flags suspicious transactions for human validation. The transaction processing pipeline also receives confirmation from the fraud analytics system before finalizing the transaction.
- Applying fraud analytics within the transaction processing pipeline: This is done with tools like Apache Flink. Flink offers event-time processing capabilities on data streams, which in the context of fraud analytics is called real-time stream processing of transaction data. It also integrates with machine learning models.
Reporting and monitoring
Stakeholders like company management, data scientists, compliance officers, fraud analysts, and security teams monitor the results of ongoing fraud detection efforts. Tools like dashboards, real-time alerts, and automated reports facilitate monitoring and supervision.
- Dashboards visually display important metrics, like the number of fraudulent transactions, the success and failure rate of the fraud analytics tools, monetary losses incurred, and more. Dashboards make it easy to highlight important information without diving into detailed reports.
- When the software suspects fraudulent activity, it sends real-time alerts to inform humans in charge of transaction monitoring. All algorithmic predictions have a certain level of confidence—in many cases, human judgment is essential for decision-making. Furthermore, in some cases, remedial measures are necessary to prevent further damage, like blocking transactions on a card suspected to be stolen. Real-time updates expedite such processes.
- Automated reports periodically collate information on the activities of fraud analytics tools. They facilitate monitoring their performance and intervening if necessary.
- Customer notifications inform customers when fraudulent activity is suspected on their accounts. Sometimes, the analytics software wrongly detects legitimate customer activity as potentially fraudulent. It is necessary to get manual confirmation from the customer before processing such transactions. In other cases, it is crucial to inform the customer that their account has been suspended due to suspicious activity and that they need to reactivate it.
Become an ML Scientist
Tools and Platforms for Fraud Analytics
Considering the significance and the widespread applications of fraud analytics, many software programs are used in this field. These include open-source tools as well as proprietary systems. In this section, we give an overview of the most common tools and platforms used in fraud analytics.
Python, SQL, and R
Customer data and transaction logs are typically stored in relational data stores.
- SQL is a powerful and flexible tool to extract relevant datasets. It allows developers to write and optimize queries to fetch datasets that meet various criteria. These datasets are analyzed to discover trends and patterns that point to potentially fraudulent activity.
- Python, due to its large ecosystem of libraries and large developer community, is often the preferred tool to build and test various analytics algorithms. More generally, Python is also used for many finance-based applications.
- Statistical analysis is at the core of many fraud detection methods. Thus, R, with its large library of statistical functions, is ideal for various kinds of ad-hoc data analyses to detect fraud.
Thus, Python, SQL, and R give developers the perfect toolset to build their custom fraud analytics systems. However, these tools can struggle with efficiently processing large datasets. The implementation of analytics systems often uses other specialized software like Apache Spark (discussed below).
Additionally, tools built on Python and SQL may not be suitable for non-technical audiences like fraud analysts and compliance officers. It is common to deliver integrated solutions built using 3rd party tools like SAS (discussed later).
Apache Spark
Many fraud analytics techniques are based on machine learning algorithms trained on transaction logs and customer datasets. Detecting patterns in real time necessitates processing large volumes of data. For example, credit card processors handle millions of transactions per day. To detect a fraud ring, the analytics system must efficiently process many days worth of transaction data.
Apache Spark is an open-source data processing engine that scales horizontally across clusters. Due to its in-memory computing capability, it can handle large datasets without resorting to batch processing.
It accepts input data from multiple data sources, such as Cassandra and Amazon S3. It also offers APIs in many languages, including Python and Java. Thus, it is uniquely suited for big data use cases like fraud analytics.
Check the Introduction to PySpark course to learn this powerful data processing language today.
Tableau and Power BI
Fraud analytics involves large datasets and complex analyses. Visualizations make it easier and faster for humans to comprehend this information. Tableau and Power BI are data visualization tools that can interface with various data sources. They are used for both reporting and analysis tasks.
- These tools create interactive dashboards to report important metrics like trends, success and failure rates, loss amounts, and transaction volumes. Visualizations can also categorize this information by different types of fraud and geographical regions.
- In addition to reporting, Power BI and Tableau also facilitate fraud analysis by visually presenting information about potential fraud rings, network analyses, and various probabilities.
- These tools also allow analysts to visually control various filters, detection criteria, and confidence levels. This helps make quick decisions on whether a transaction is genuine or fraudulent.
These tools are designed as general-purpose visualization tools with specific modules and user interfaces for fraud analytics. You can start learning PowerBI today by following the PowerBI Fundamentals skill track.
SAS Fraud Management
SAS is a statistical software suite built by the SAS Institute. The institute also makes domain-specific packages for various applications, including fraud analytics.
SAS Fraud Management uses statistical techniques and machine learning algorithms to predict and prevent fraud. These algorithms are productized so that people, like fraud analysts and compliance officers who don’t have a background in machine learning, can also use ML and statistical methods for fraud detection.
H2O.ai
H2O.ai offers an automated cloud-based machine learning service. H2O.ai’s software flags potentially fraudulent activity, scores the likelihood of fraud and assigns a reason code to indicate why the algorithm suspects fraud.
These guidelines help human investigators dig deeper to verify the transaction. In many cases, they also help greenlight genuine transactions to speed up their processing.
IBM Safer Payments
IBM Safer Payments is a fraud detection system specifically targeted to the payments industry.
Since it uses a NoSQL in-memory database, it can monitor payments in real time. It prevents fraud in cashless payment systems, such as credit card payments, by analyzing transaction streams in real time and blocking potentially fraudulent transactions before they are executed.
Conclusion
This article provided an overview of different kinds of fraud and the role of fraud analytics in detecting and preventing them. It discussed techniques commonly used to detect cases of potential fraud and the fraud detection workflow. Finally, the article introduced some software applications commonly used in this domain.
To learn how to build fraud detection systems using Python, go through the course Fraud Detection in Python. To get a broad-based introduction to Python for finance applications, follow the course Introduction to Python for Finance. To learn more about the statistics functions in R used for fraud detection applications, follow the course Fraud Detection in R.
Get Certified in Data Science
Validate your professional data scientist skills.
FAQs
Can fraud analytics completely eliminate fraud?
No, fraud analytics significantly reduces fraud but can’t eliminate it entirely. It helps flag high-risk transactions, but human oversight is still needed.
How do businesses handle flagged transactions in real time?
Flagged transactions are often reviewed by human investigators. Automated systems may also block suspicious transactions pending further review.
What data is crucial for effective fraud detection?
Key data includes transaction logs, customer profiles, third-party validation sources, and device data. High-quality, clean data improves detection accuracy.
How do unsupervised machine learning models evolve with new fraud patterns?
Unsupervised models continuously adapt to new behaviors by identifying unknown patterns and anomalies, making them more effective at detecting emerging fraud methods.
How do fraud detection systems balance speed and accuracy?
Systems use real-time data processing tools like Apache Flink to analyze transactions instantly while minimizing false positives by refining algorithms over time.
Arun is a former startup founder who enjoys building new things. He is currently exploring the technical and mathematical foundations of Artificial Intelligence. He loves sharing what he has learned, so he writes about it.
In addition to DataCamp, you can read his publications on Medium, Airbyte, and Vultr.

